Overview
This document reviews the applicable configuration of the Decisions platform for PCI compliance in the order of PCI DSS 4.0 requirements. This is important for any use case that processes credit card data. Please note hardware setup is out of scope for this article.
There are many parts to PCI compliance, this document will only touch upon the ones that are applicable and will do so in the order that they appear as of PCI DSS 4.0. For instance, this document will not discuss how to set up hardware to meet PCI requirements.
This document is also ordered by how the PCI compliance report is laid out and the section numbers correspond to requirements on their checklist.
Part I
4.2 - Account Data Flow Diagrams
A visual diagram of any Flow can be easily downloaded. Right-click a Flow, then selected OTHER | Advanced > View History.
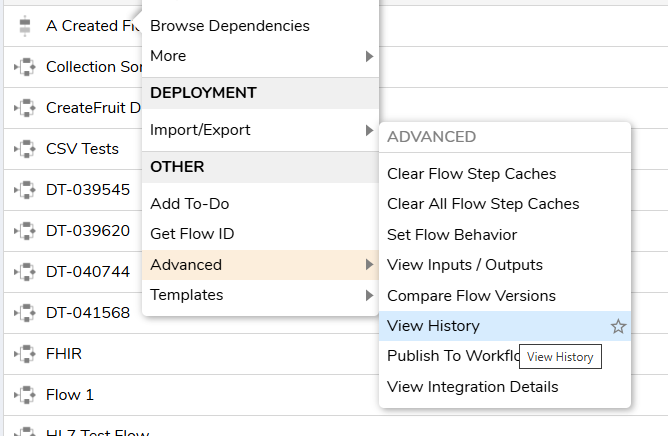 The History and Documentation screen for the Flow will appear in a new tab. Then press the DOWNLOAD button under Folder Data to create a .PNG file of the Flow.
The History and Documentation screen for the Flow will appear in a new tab. Then press the DOWNLOAD button under Folder Data to create a .PNG file of the Flow.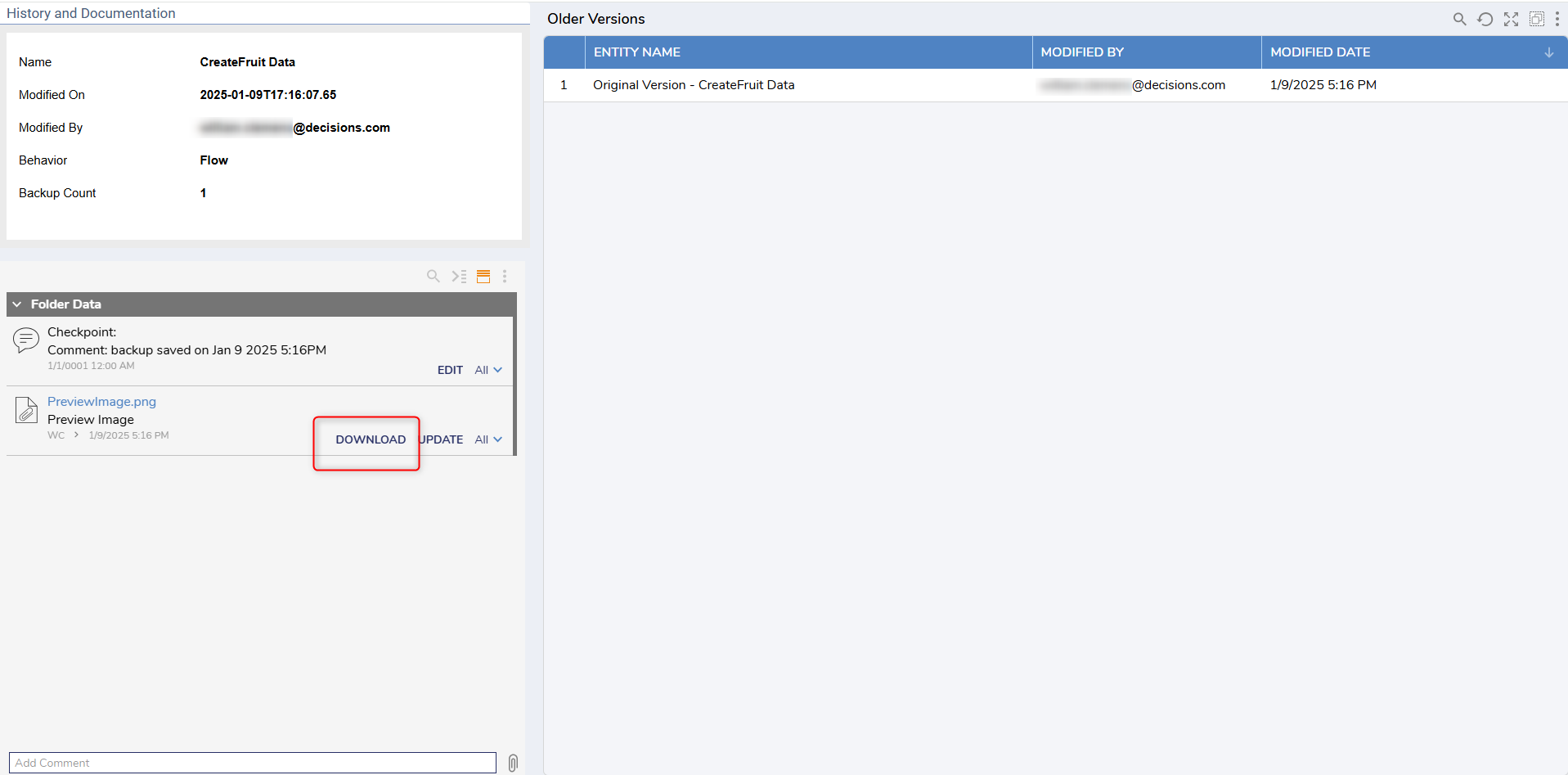
4.3 - Storage of Account Data
Users have many strategies at their disposal when it comes to storing data. Customers that use Decisions hosting should know that they have complete control over their data retention policies and Decisions staff do not delete anything.
There are various methods of managing how long data is kept, and its permanent deletion can be configured and maintained via scheduled jobs.
Customers can use any kind of database integration, both internal and external databases. Data created via Flow requires explicit logic to save that data.
Part II
1.1 - "Processes and mechanisms for installing and maintaining network security controls are defined and understood."
Decisions supports several methods of network security. The platform allows for HTTPS, secure cookies, WIS credentials and more. All details about these settings can be found in the Securing a Decisions Installation article.
1.2 - "Network security controls (NSCs) are configured and maintained."
Most network security settings are configured during installation. HTTPS, for instance is configured at that time. These settings can also be adjusted at anytime by editing the settings.xml file.
1.3 - "Network access to and from the cardholder data environment is restricted."
Database access can be secured in a number of ways. Database integration is handled at the Project level and building configurations can be limited to specific Users or groups of Users. An organization could create a single Project that only the DBA or other authorized user could view. Then other Projects could use needed data from that Project through a dependency.
1.4.3 - "Anti-spoofing measures are implemented to detect and block forged source IP addresses from entering the trusted network."
IP addresses can be specified to be blocked in the System settings. Either IP addresses can be blocked per Account to prevent access by a User, or IP addresses can be blocked platform-wide by editing the settings.xml file.
2.2 - "System components are configured and managed securely."
All System level settings and configurations are only available to users with Administrator permissions by default.
2.2.2 - "Vendor default accounts are managed as follows:
If the vendor default account(s) will be used, the default password is changed per Requirement 8.3.6.
If the vendor default account(s) will not be used, the account is removed or disabled."
Decisions comes with the default account admin@decisions.com. It is recommended to change the password upon installation.
2.2.3 - "Primary functions requiring different security levels are managed as follows:
Only one primary function exists on a system component, OR
Primary functions with differing security levels that exist on the same system component are isolated from each other, OR
Primary functions with differing security levels on the same system component are all secured to the level required by the function with the highest security need."
Users can create accounts with different levels of access. By default only Administrators have access to any System settings.
2.2.7 - "All non-console administrative access is encrypted using strong cryptography."
All administrative access is handled through account permissions.
3.1 - "Processes and mechanisms for protecting stored account data are defined and understood."
User account information is only available to users with Administrator access.
3.3 - "Sensitive authentication data (SAD) is not stored after authorization"
Flow logic can be configured to prevent any kind of collected data from being stored.
3.3.2 - "Examine data stores, system configurations, and/or vendor documentation to verify that all SAD that is stored electronically prior to completion of authorization is encrypted using strong cryptography."
Decisions supports robust cryptography with an AES 256 algorithm.
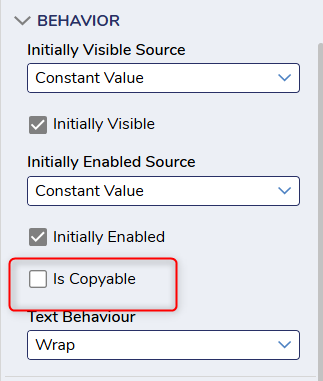
3.4 - "Access to displays of full PAN and ability to copy PAN is restricted."
If displaying PAN on a Form, that data can be prevented from being copied by using the "Is Copyable" setting under BEHAVIOR in the Form Designer. Toggling it off will prevent data from being selectable and copyable.
3.5 - "Primary account number (PAN) is secured wherever it is stored."
Data generated from a Flow can be encrypted and securely stored as needed. When building Flows, Users have access to steps such as Hash String With SHA 256 and Hash String With SHA 512 so that any data they create can be encrypted.
3.6 - "Cryptographic keys used to protect stored account data are secured."
Users have control over encryption key rotation. Keys are configured under System > Administration > Encryption. There are two kinds of keys available, one type for data structures and the second handles system wide areas such as passwords, connection strings, and SMTP settings. Keys can be rotated manually.
3.7 - "Where cryptography is used to protect stored account data, key management processes and procedures covering all aspects of the key lifecycle are defined and implemented."
Users have control over encryption key rotation. Keys are configured under System > Administration > Encryption. There are two kinds of keys available, one type for data structures and the second handles system wide areas such as passwords, connection strings, and SMTP settings.
There are additional Dashboards with Reports on key as well. Any problems that arise will appear in the Encryption Issues Page and its accompanying Issue Resolution History. Key Rotation Audit will show every time a key rotation has occurred. And a list of all available keys and their encryption level is under the Keys page.
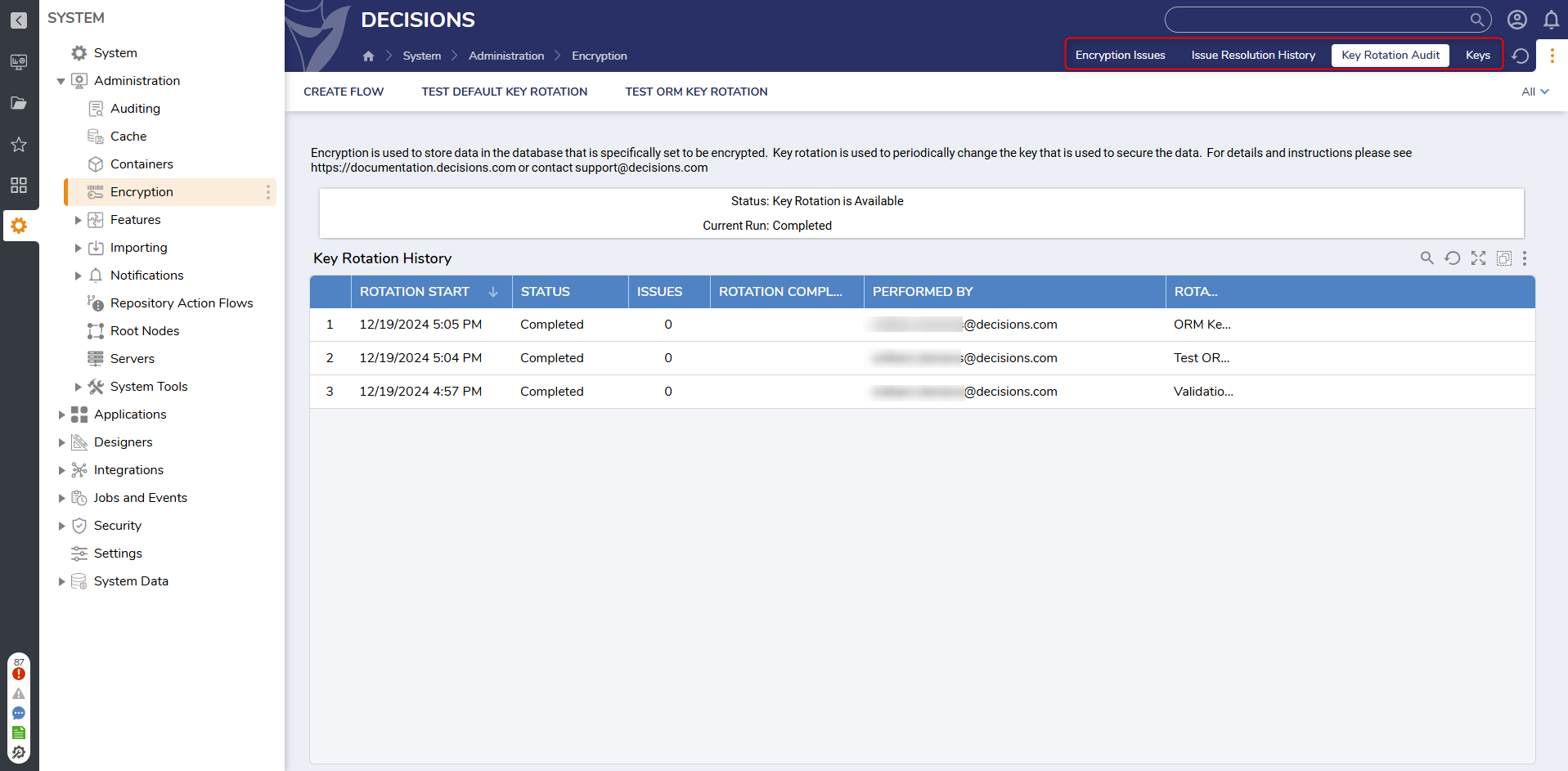
This will also cover the requirement in 3.7.2: "Key-management policies and procedures are implemented to include secure distribution of cryptographic keys used to protect stored account data."
4.1 - "Processes and mechanisms for protecting cardholder data with strong cryptography during transmission over open, public networks are defined and documented."
Decisions supports robust cryptography with an AES 256 algorithm. When building Flows, Users have access to steps such as Hash String With SHA 256 and Hash String With SHA 512 so that any data they create can be encrypted. We also provide support for PGP with the PGP Module.
4.2 - "PAN is protected with strong cryptography during transmission."
Decisions supports robust cryptography with an AES 256 algorithm. When building Flows, Users have access to steps such as Hash String With SHA 256 and Hash String With SHA 512 so that any data they create can be encrypted. We also provide support for PGP with the PGP Module.
Additionally, Users can create encrypted Project Constants. The constants can be used in any number of Flows within a Project without revealing the set value. Not only is the constant only editable by selected accounts, but because the constant is limited to a specific Project, the number of Users would could interact with it is also locked down. The Secured Constant type is the Project Constant with encryption.
4.2.2 - "PAN is secured with strong cryptography whenever it is sent via end-user messaging technologies."
We recommended using the PGP Module to provide secure messaging.
5.1 - "Processes and mechanisms for protecting all systems and networks from malicious software are defined and understood."
Decisions supports the use of HTTPS and strong encourages its use. In v9.6 nonce support was added to protect against cross-site scripting attacks. To learn about setting up HTTPS for IIS installations, click here. For self-hosted installations, click here.
6.2 - "Bespoke and custom software are developed securely."
Decisions provides Users with the ability to add new functionality to their builds through the SDK and the various scripting modules. Users should be aware that Administrators need to acknowledge and accept full responsibility for securing the environment ahead of installing and using either feature.
6.3 - "Security vulnerabilities are identified and addressed."
Decisions is continuously monitoring for vulnerabilities and providing patches when needed. We strongly encourage users to upgrade to the newest version for the most robust protection.
6.4 - "Public-facing web applications are protected against attacks."
Decisions supports SSL and HTTPS to reduce the danger of attacks. HTTPS can be established on installation, or at any time by configuring the settings.xml file. Emails sent through the platform can be configured to use explicit SSL by modifying the settings.xml file.
6.5 - "Changes to all system components are managed securely."
Only Administrator level users have access to the System section of a Decisions platform. Only those Users are able to provide Administrator permissions.
7.2 - "Access to system components and data is appropriately defined and assigned."
Only Administrator level users have access to the System section of a Decisions platform. All Projects can be given unique access so that each role has clearly defined areas they can access.
7.3 - "Access to system components and data is managed via an access control system(s)"
Only Administrator level users have access to the System section of a Decisions platform. All Projects can be given unique access so that each role has clearly defined areas they can access.
8.2 - "User identification and related accounts for users and administrators are strictly managed throughout an account’s lifecycle."
Administrators have access to create and delete user accounts at any time. These are located under System > Security > Accounts. Accounts have a 'Created On' date so that the age of an account can be viewed. See Deactivating and Activating a User Account for more detail.
Tailored end user access is also available through the use of Guest Accounts. See Enabling a Guest Account.
8.3 - "Strong authentication for users and administrators is established and managed."
PCI compliance requires that passwords be a minimum of 12 characters and contain numeric and alphabetic characters. Password policy can be changed under System > Settings > Portal Settings. For more see Changing Password Policy.
8.4 - "Multi-factor authentication (MFA) is implemented to secure access into the CDE."
Decisions supports MFA both through the platform and through 3rd party integration with Okta and OpenID. To learn more about how to set up 2FA, see this article.
8.5 - "Multi-factor authentication (MFA) systems are configured to prevent misuse."
Decisions MFA functionality can be configured as needed. Token length and the amount of time a token is valid can be customized. PCI does not have any specific requirements for token length or expiration. See Setting up 2FA for more details on how to make these configurations.
8.6 - "Use of application and system accounts and associated authentication factors is strictly managed."
Users are able to view which accounts are actively accessing the platform at any time. Go to System > System Tools > Event Viewer and click the Active Users Page. In addition, Administrators can also view all logins over time. This is located under the Event Viewer as well on the Accounts Login Page.
10.1 - "Processes and mechanisms for logging and monitoring all access to system components and cardholder data are defined and documented."
Only Users with Administrative permissions are able to access system components and all settings for logs and system monitoring.
10.2 - "Audit logs are implemented to support the detection of anomalies and suspicious activity, and the forensic analysis of events."
Decisions provides a vast suite of log options. To learn more, read Logging Overview.
10.3 - "Audit logs are protected from destruction and unauthorized modifications."
Usage logs are kept automatically by Decisions. By default only 10 log files are kept at any time before they are overwritten. However, Users can change this by modifying the Logging Settings.
10.6 - "Time-synchronization mechanisms support consistent time settings across all systems."
All Decisions servers are time-synchronized. Users are given the ability to customize how time is displayed. Users with the proper permissions are able to see what the server time is at any moment by going to the account icon in the top right corner and pressing About.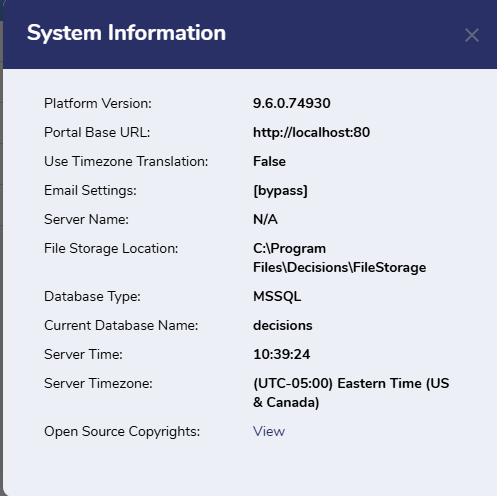
Please review the following documents about time display settings in Decisions:
References
Accounts
- Changing Password From Administrator & User Account
- Changing Password Policy
- Creating Groups
- Deactivating and Activating a User Account
- Enabling a Guest Account
- Permissions Overview
- Project Dependencies
- Project Permissions
Encryption/Data Security
- Encryption Key Rotation
- Encryption Overview
- Hash String With SHA 256
- Hash String With SHA 512
- PGP Module
- Project Constants
Logs
Network Security
- Configuring Server for HTTPS Redirection
- Configuring Server for SSL (HTTPS)
- Email and SMTP in Decisions
- Installing and Configuring the Okta Module
- IP Address Filtering
- MFA
- OpenID Integration
- Securing a Decisions Installation
- Settings.xml Overview
- Setting Up 2FA
- Setting up Date/Time Translation
- Timeszones Overview