Overview
Decisions facilitate efficient logging through AWS CloudWatch integration, enabling seamless tracking of logs from a container via AWS. AWS CloudWatch Logs, a vital feature of AWS CloudWatch, enables monitoring, storage, and access to log files from diverse AWS resources, applications, and custom log files. This centralized approach simplifies the monitoring and troubleshooting of various systems and applications.
| Benefits of using AWS CloudWatch | Description |
|---|---|
| Centralized Monitoring | AWS CloudWatch Integration allows the organization to centralize log data, providing a unified view of application performance and behavior. |
| Real-Time Insights | The real-time monitoring and analysis capabilities of AWS CloudWatch enable proactive identification of potential issues, allowing the team to address any emerging concerns swiftly. |
| Customized Log Management | The organization can tailor log collection and monitoring based on specific requirements with customizable logging settings, ensuring efficient and targeted log management. |
| Enhanced Security | The capability to override default credentials ensures secure access to AWS CloudWatch, maintaining the integrity and confidentiality of log data. |
| Streamlined Troubleshooting | By organizing logs within CloudWatch using log group paths and log names, admin users can efficiently navigate and identify logs associated with different components of the application, streamlining the troubleshooting process. |
Prerequisites
Before setting up AWS CloudWatch Integration, ensure the following prerequisites are in place:
- Preexisting AWS Account
- Preinstalled AWS Module
- Preconfigured AWS Container
Logging Settings
Logging settings can be configured as follows:
- From the Decisions Studio, navigate to System > Settings > Logging Settings, open AWS CloudWatch.
- From the AWS CloudWatch window, select the desired Levels. Then, apply the proper fields within their respective settings.
- Restart Decisions, then navigate to the Decisions Log group in AWS under the Logs category; observe that Logging has occurred.
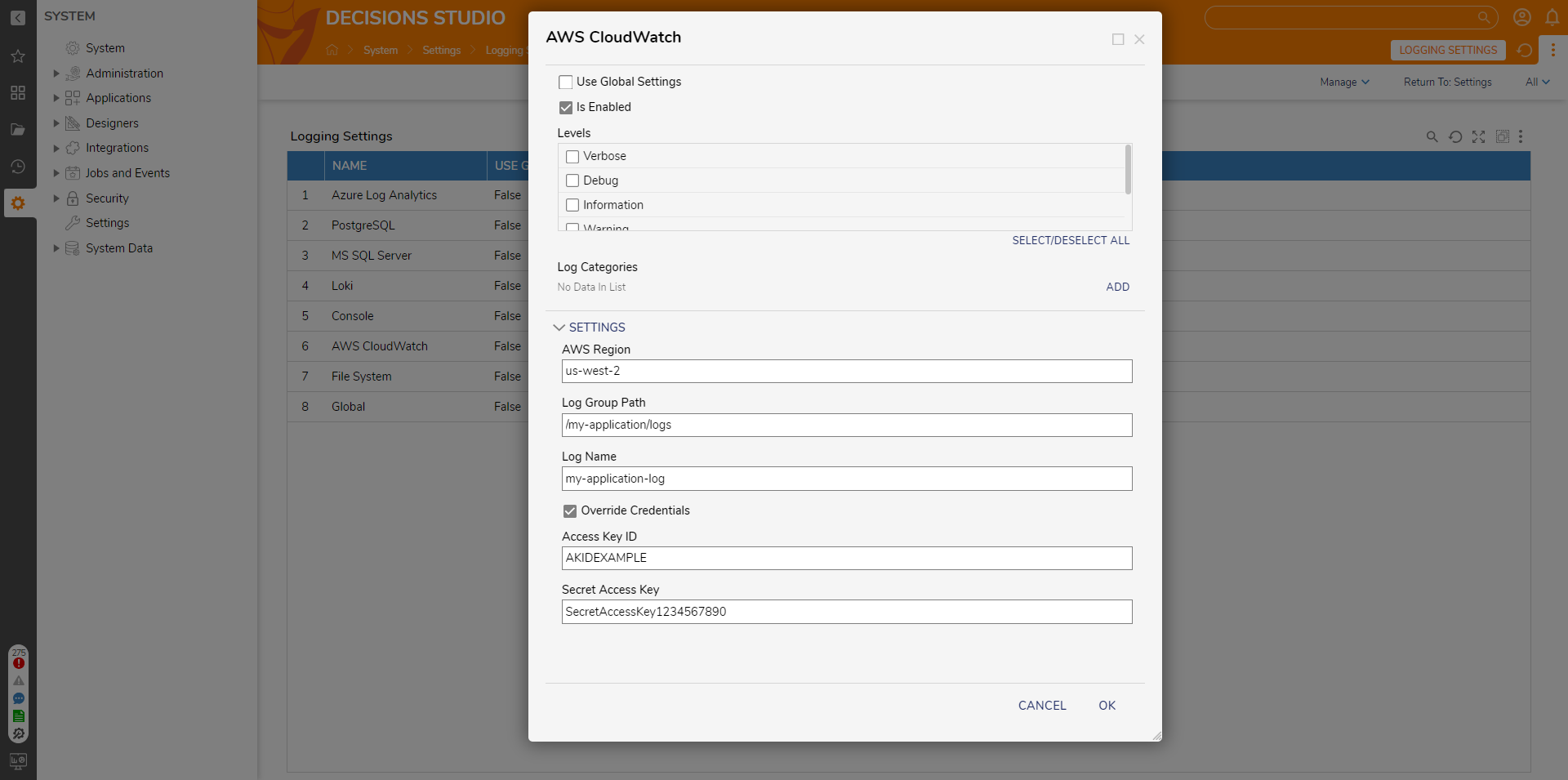
AWS Cloud Watch Settings
Here's a breakdown of the available AWS Cloud Watch settings:
Environment Variables for AWS Cloud Watch
Admin users can configure the AWS Cloudwatch in containers by passing the AWS Environment Variables. For more information, refer to Decisions Environment Variables.
| Setting | Description |
|---|---|
| Use Global Settings | Available for any logging level that is not Global. If enabled, properties defined for the logging level will be overwritten by what is defined under the Global level. |
| Is Enabled | This setting determines whether AWS CloudWatch logging is enabled for the application. If enabled, the application will send logs to AWS CloudWatch. If disabled, no logs will be sent to AWS CloudWatch, even if other settings are configured. |
| Levels | This setting defines what information will be recorded within the logs. By default, only Warning, Error, and Fatal are enabled. "Verbose" offers comprehensive details, "Debug" captures most exceptions, "Information" provides general event data, "Warning" monitors potential issues, "Error" tracks process failures, and "Fatal" issues critical warnings that can disrupt the environment by halting processes. |
| Log Categories | Selecting Add will open another dialog box where log categories can be selected. If a category is defined, then only information from the related category will appear. |
| AWS Region | The AWS Region specifies the geographical location where the CloudWatch logs will be stored. Choose the AWS Region that is closest to your application to minimize latency and data transfer costs. It is an important setting for ensuring efficient log management. |
| Log Group Path | The Log Group Path defines the grouping or categorization of logs within AWS CloudWatch. This setting helps organize and structure the logs within CloudWatch. Typically, you can create a hierarchical structure for logs by specifying a log group path, which makes it easier to manage and search for specific logs. |
| Log Name | The Log Name is the unique identifier for a specific log stream within the specified log group. Setting the log name helps identify and differentiate logs generated by different parts of your application. |
| Override Credentials | This setting overrides the default credentials used to authenticate with AWS CloudWatch. When enabled, provide custom AWS access credentials to ensure secure access to the CloudWatch service. |
| Access Key ID | The Access Key ID is part of the AWS access credentials used for authentication with AWS CloudWatch. It is a unique identifier associated with the AWS account. Specify the Access Key ID when overriding credentials. |
| Secret Access Key | The Secret Access Key is the other part of the AWS access credentials, used in conjunction with the Access Key ID for secure authentication with AWS CloudWatch. Keep this key confidential and secure, as it is a sensitive piece of information required for AWS access. Specify it when overriding credentials. |
Feature Changes
| Description | Version | Developer Task |
|---|---|---|
| Allow for AWS credentials in AWS CloudWatch Logging Settings | 8.15 | [DT-034351] |