Overview
Warning
Configuring Single Sign-On involves very detailed settings that vary with every provider and customer environment. These settings are strict and must be at the knowledge of the administrator configuring the connection. If SSO is a new concept, it may take time and multiple attempts to accurately configure all of the identifying data and settings, allowing for secure and reliable authentication. The Decisions Support team is available to help, but may not be able to answer questions or solve problems that are unique to a customer organization.
Accounts created before the following module is installed will need to be updated before using Single Sign-On. Please contact support on how to update the account. Learn how to modify accounts after setting up SSO in the SSO Basics article.
Prerequisites
- SAML module installed. To learn how to install a module, see Installing Modules in Decisions.
- Logout URL
- Login URL
- NameId Policy (Email or TransientID)
- User ID Attribute Name (only needed if NameId policy is Transient)
- X.509 Certificate in PEM format. Below is an example of a PEM formatted string
-----BEGIN CERTIFICATE----- MIIB9TCCAWACAQAwgbgxGTAXBgNVBAoMEFF1b1ZhZGlzIExpbWl0ZWQxHDAaBgNV BAsME0RvY3VtZW50IERlcGFydG1lbnQxOTA3BgNVBAMMMFdoeSBhcmUgeW91IGRl Y29kaW5nIG1lPyAgVGhpcyBpcyBvbmx5IGEgdGVzdCEhITERMA8GA1UEBwwISGFt aWx0b24xETAPBgNVBAgMCFBlbWJyb2tlMQswCQYDVQQGEwJCTTEPMA0GCSqGSIb3 DQEJARYAMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCJ9WRanG/fUvcfKiGl EL4aRLjGt537mZ28UU9/3eiJeJznNSOuNLnF+hmabAu7H0LT4K7EdqfF+XUZW/2j RKRYcvOUDGF9A7OjW7UfKk1In3+6QDCi7X34RE161jqoaJjrm/T18TOKcgkkhRzE apQnIDm0Ea/HVzX/PiSOGuertwIDAQABMAsGCSqGSIb3DQEBBQOBgQBzMJdAV4QP Awel8LzGx5uMOshezF/KfP67wJ93UW+N7zXY6AwPgoLj4Kjw+WtU684JL8Dtr9FX ozakE+8p06BpxegR4BR3FMHf6p+0jQxUEAkAyb/mVgm66TyghDGC6/YkiKoZptXQ 98TwDIK/39WEB/V607As+KoYazQG8drorw== -----END CERTIFICATE-----
Version 5 and 6 Endpoints
LoginURL - [base]/Login.aspx
LogoutURL - [base]/Logout.aspx SAML - [base]/SAML/AssertionConsumer.ashx
TokenHandler - [base]/HandleTokenResponse.aspx
Example: localhost/decisions/Logout.aspx
LogoutURL - [base]/Logout.aspx SAML - [base]/SAML/AssertionConsumer.ashx
TokenHandler - [base]/HandleTokenResponse.aspx
Example: localhost/decisions/Logout.aspx
Warning
Users cannot set up Active Directory Sync simultaneously with Single Sign-On (via SAML and OpenID Modules). Doing so will result in an error that requires users to reset their sign-on setup. At least one Admin user must be configured beforehand to work with SAML SSO, otherwise, there will be no admin users who can log into the System after enabling. When SSO is enabled, no local users can log in. If this is accidentally done, disable SSO and then log in with local users.
Example
This example will demonstrate how to configure Single Sign-On using the SAML module.
- Navigate to the System> Settings. Right-click SAML Settings and select Edit.
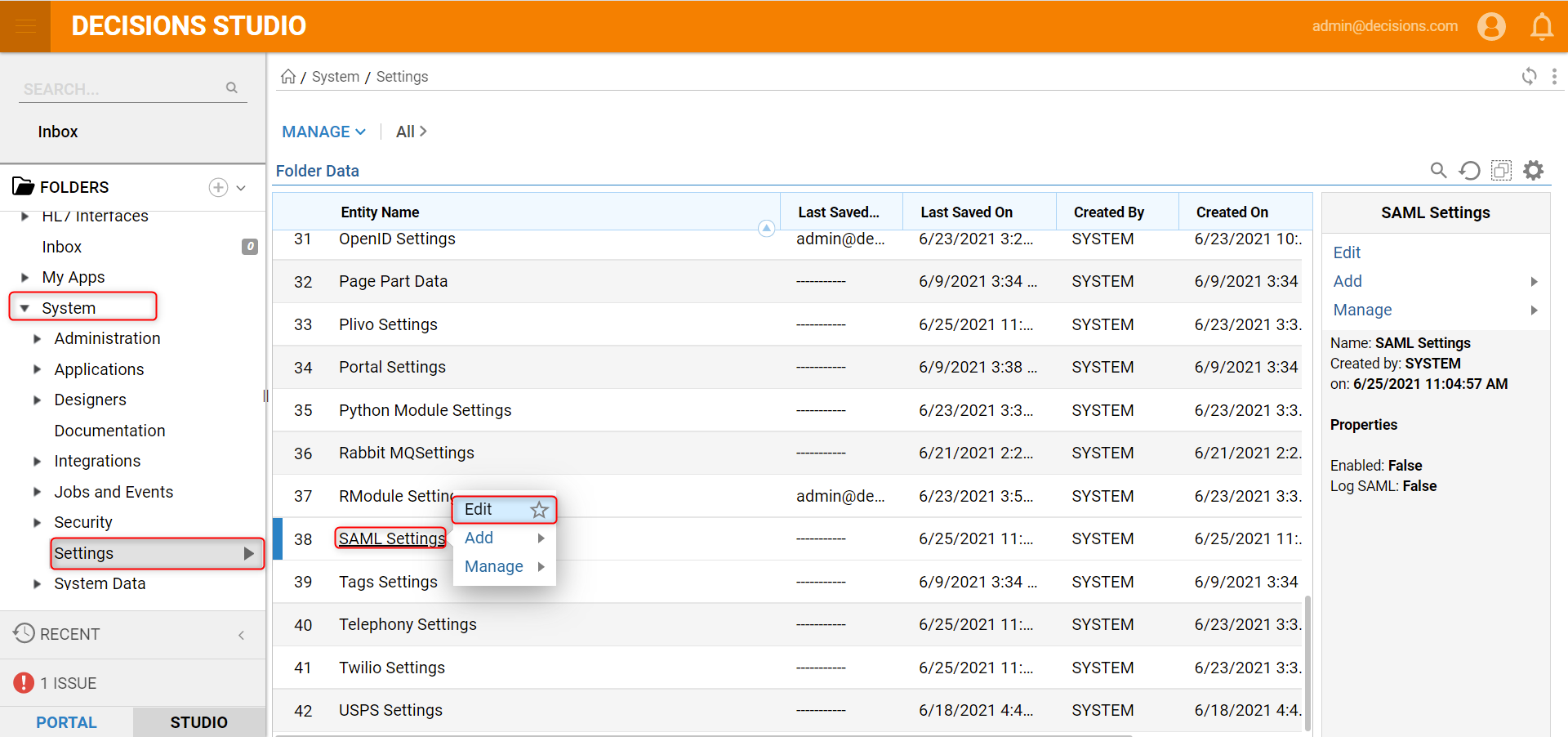
- In the Edit SAML Settings window under SAML Integration, check the Enabled option. Then, in the Identity Providers section, select Add New.
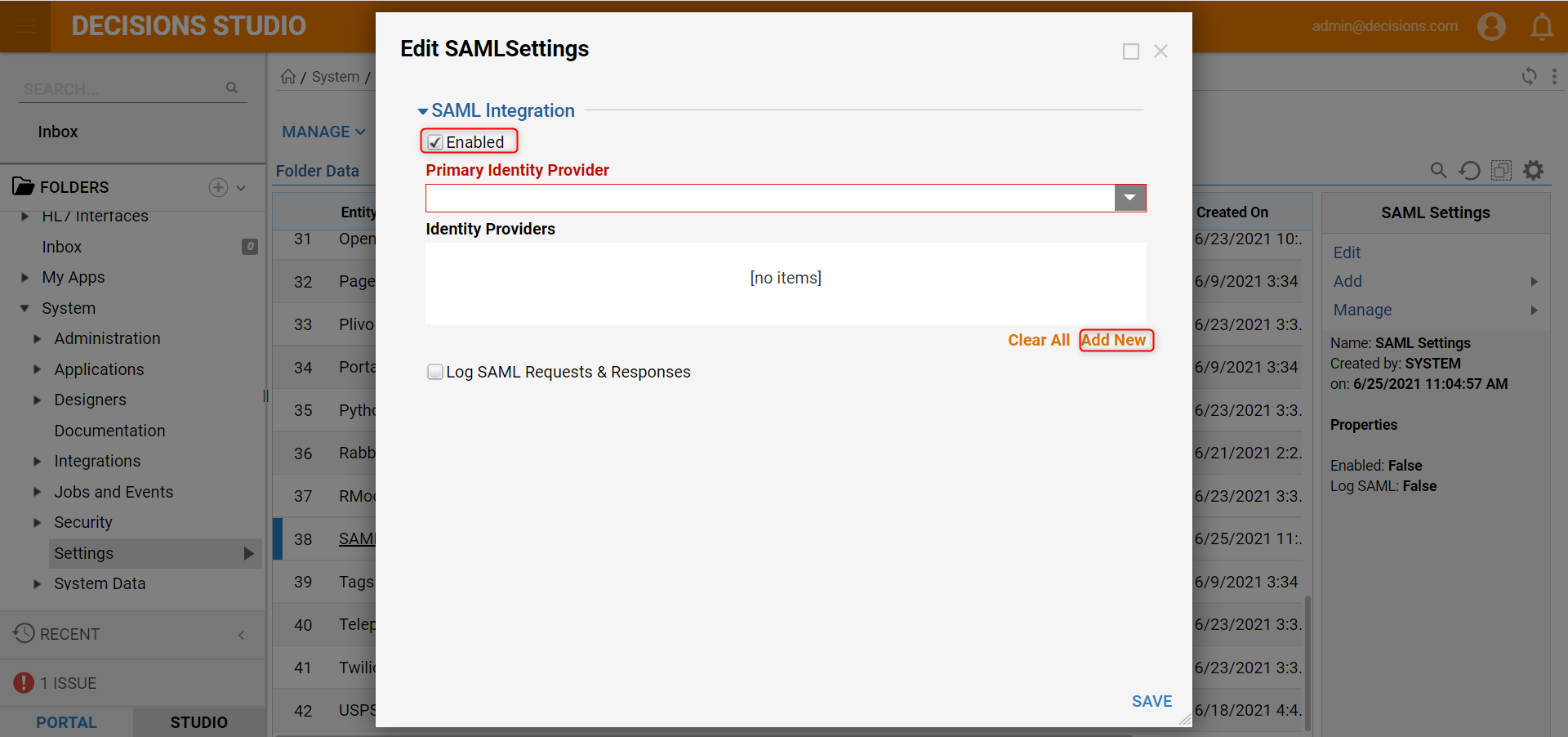
- Configure the appropriate fields in the Edit Identity Providers window. This information is based on the SSO provider information used for the organization. When complete, click OK.
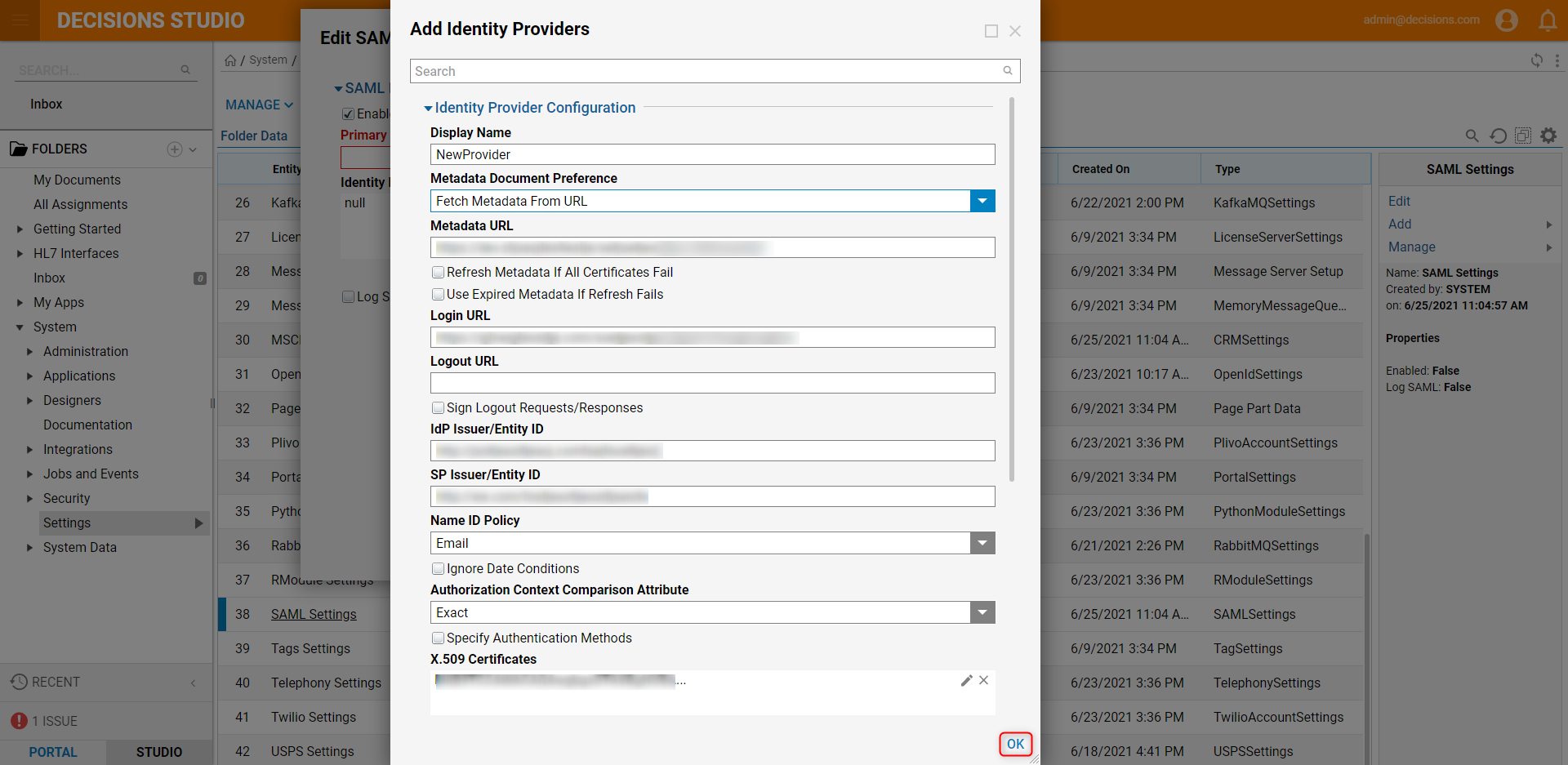
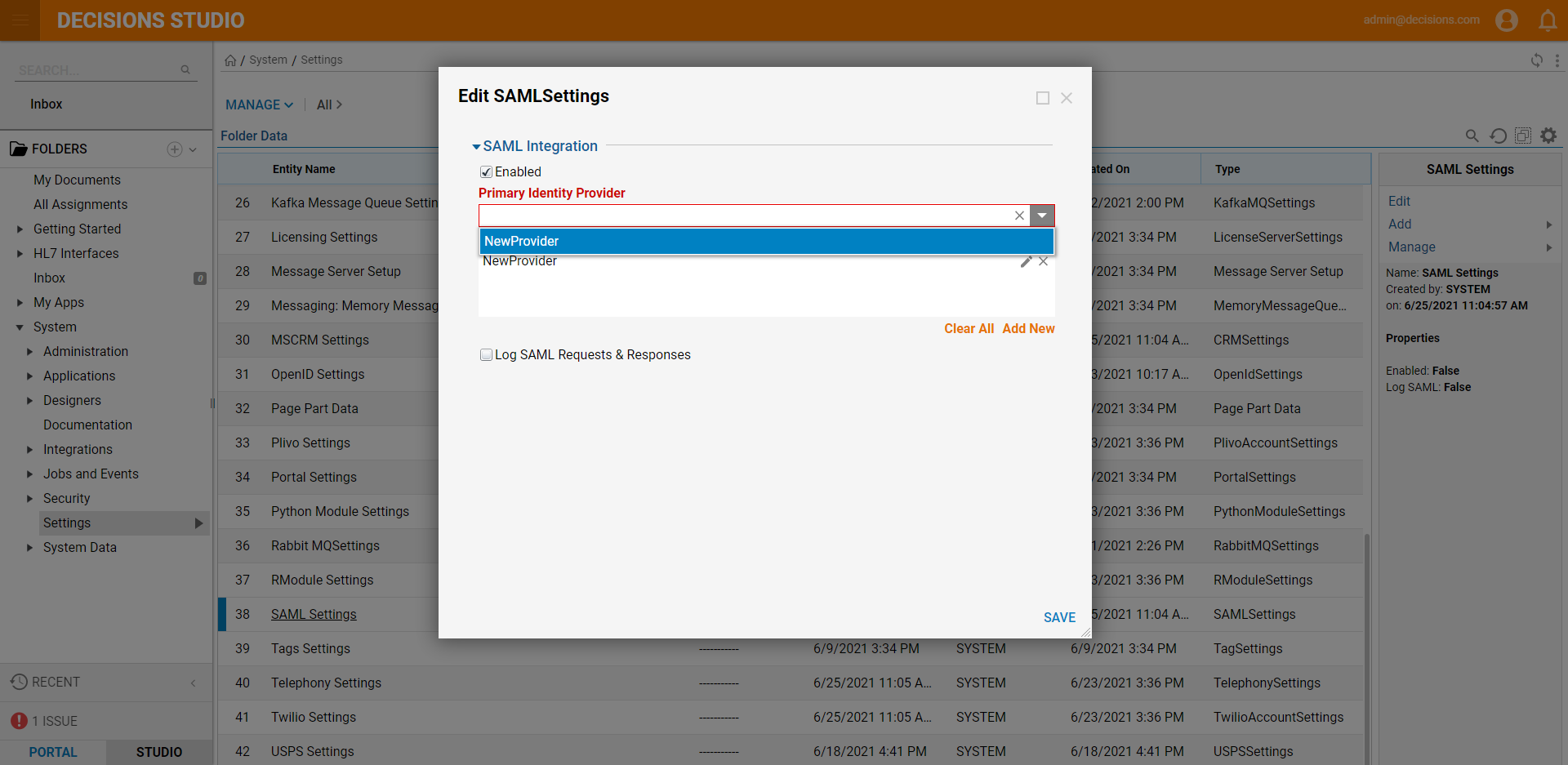
Setting Name Description Display Name Name for Identity Provider Login URL The SSO login of the Identity Provider Logout URL The SSO logout URL of the Identity Provider Sign Logout Requests/Responses When set to true, logouts will be signed with a private certificate. Logout Signature Algorithm RSA-SHA1 and RSA-SHA256 are the available signature algorithms. Filename of PFX File Path to the private cert file on the server's filesystem. Password for PFX Password for the private cert IdP Issuer/Entity ID The ID of the identity provider. This value is only required to allow Identity Provider initiated logins. SP Issuer/Entity ID Usually, the Base URL to the Decisions Portal. The Portal Base URL can be found by clicking the Profile icon in the Designer Studio, then selecting About from the menu. Name ID Policy Either email or transient ID based on Identity Provider X.509 Certificate The PEM formatted string of the X.509 cert Process If User Not Found When enabled, the selected Flow will be run if a user with an unknown ID tries to log in. This Flow is typically used to create the unknown user in the Decisions Portal so that they can log in. Processing Type Set to Run Flow In Background. Pick Flow This is the Flow that will be run when an unknown user tries logging in. The default Flow can be used for creating unknown users. It is named SAMLDefaultCreateAccount. Retry Login After When set to true, the System will try to log in the user after running the selected Flow. If the Flow creates the user, it should be set to be true so that the user seamlessly gets logged in, or else they would have to try logging in a second time to get in. - In the Edit SAML Settings window, click the dropdown list under Primary Identity Provider and select the created Identity Provider. Select 'Ok' and Save to save SAML Settings.
 When using a SAML Login Flow from the option Run Flow on Each Login, Relay State is available as input in the Flow Designer on the Data Explorer panel. Auto Timeout should only be used with the built-in SignOn. In the HTML Portal, logout the user, hence they go back to their SSO Sign-in Page, and it would work. To get Attributes passed in from the SAML Response, navigate to the Data Explorer panel then SAML Response > Assertion > AttributeStatement.
When using a SAML Login Flow from the option Run Flow on Each Login, Relay State is available as input in the Flow Designer on the Data Explorer panel. Auto Timeout should only be used with the built-in SignOn. In the HTML Portal, logout the user, hence they go back to their SSO Sign-in Page, and it would work. To get Attributes passed in from the SAML Response, navigate to the Data Explorer panel then SAML Response > Assertion > AttributeStatement.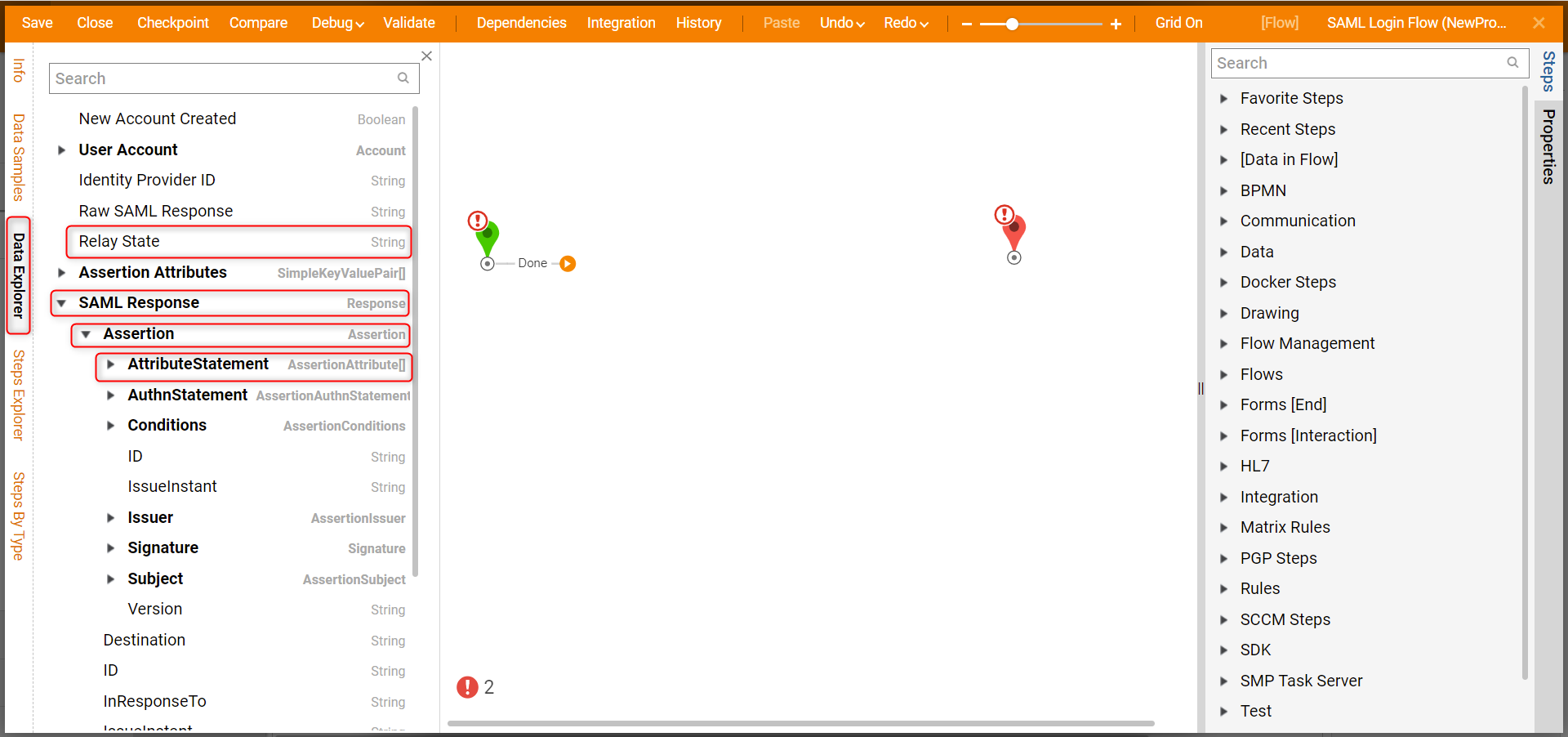
- Navigate to System> Security > Accounts and right-click an account that should be able to use SAML SSO. Select Edit Account.
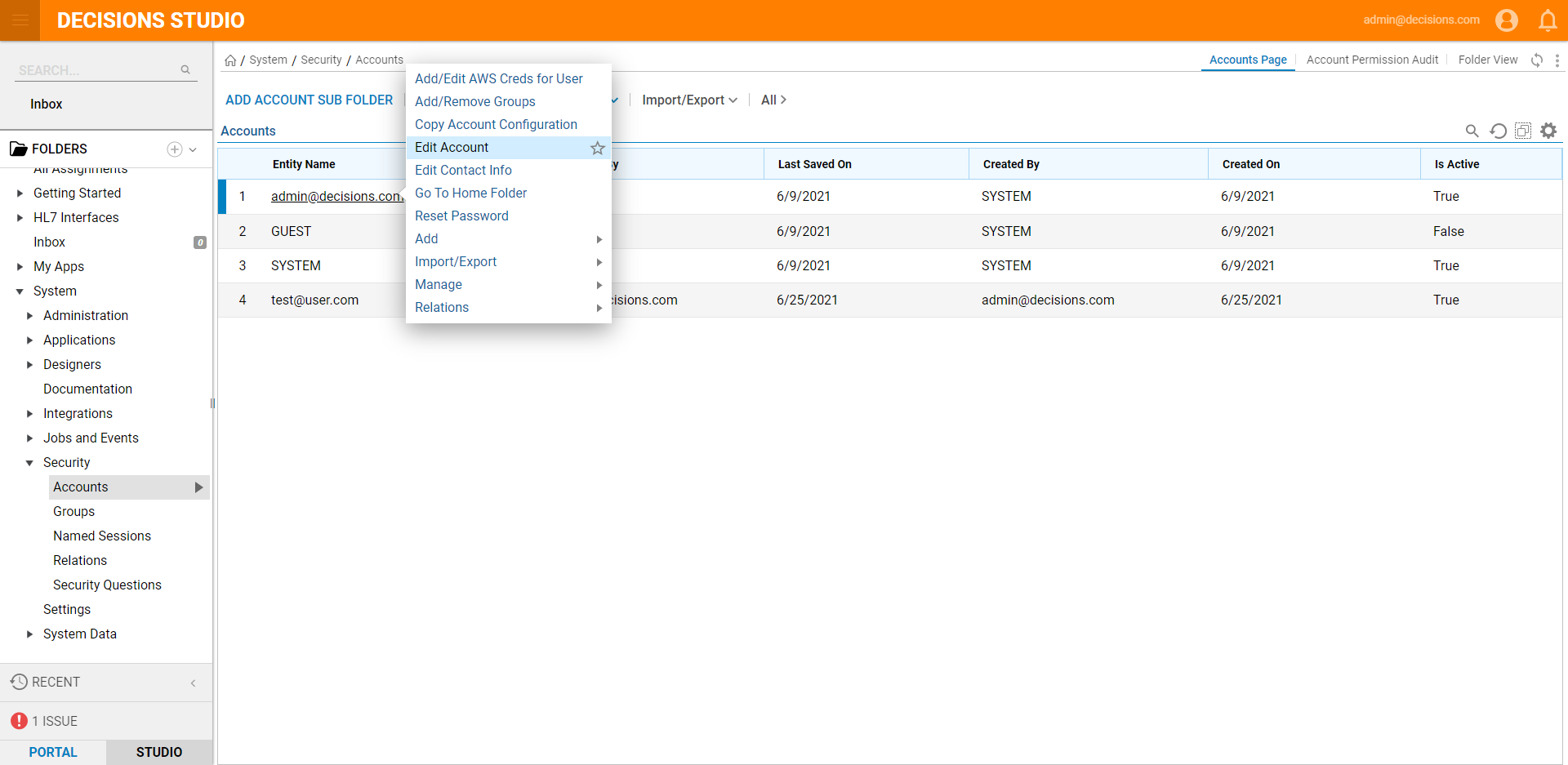
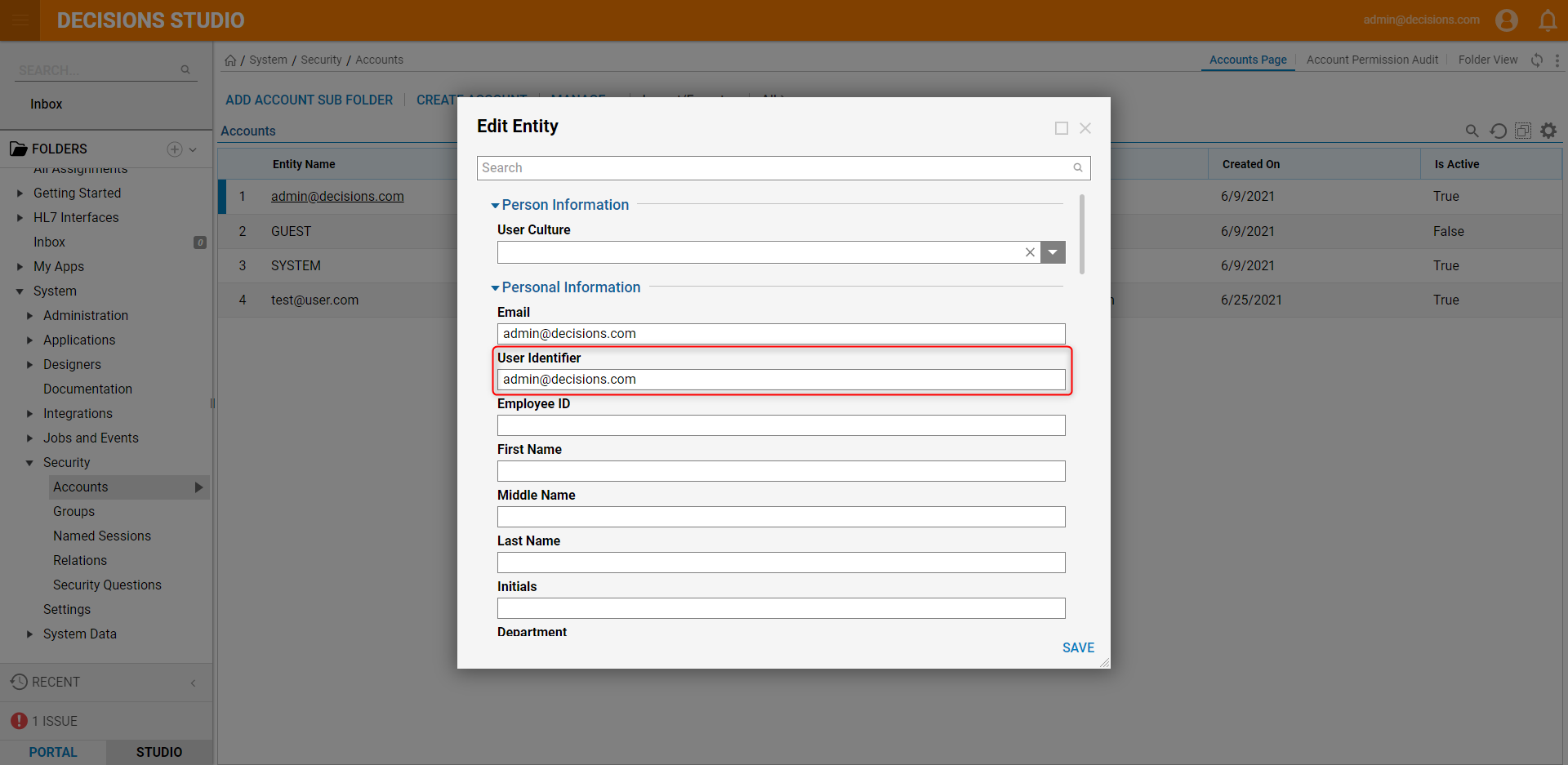
- In the Edit Account resulting window, locate the Personal Information section and define the User Identifier value. This value should be used as the value for the Identity Provider to send as the User Id.
- Once at least one admin user is enabled to work with SSO, open the Settings.xml file located at C:\Program Files\Decisions\Decisions Services Manager.
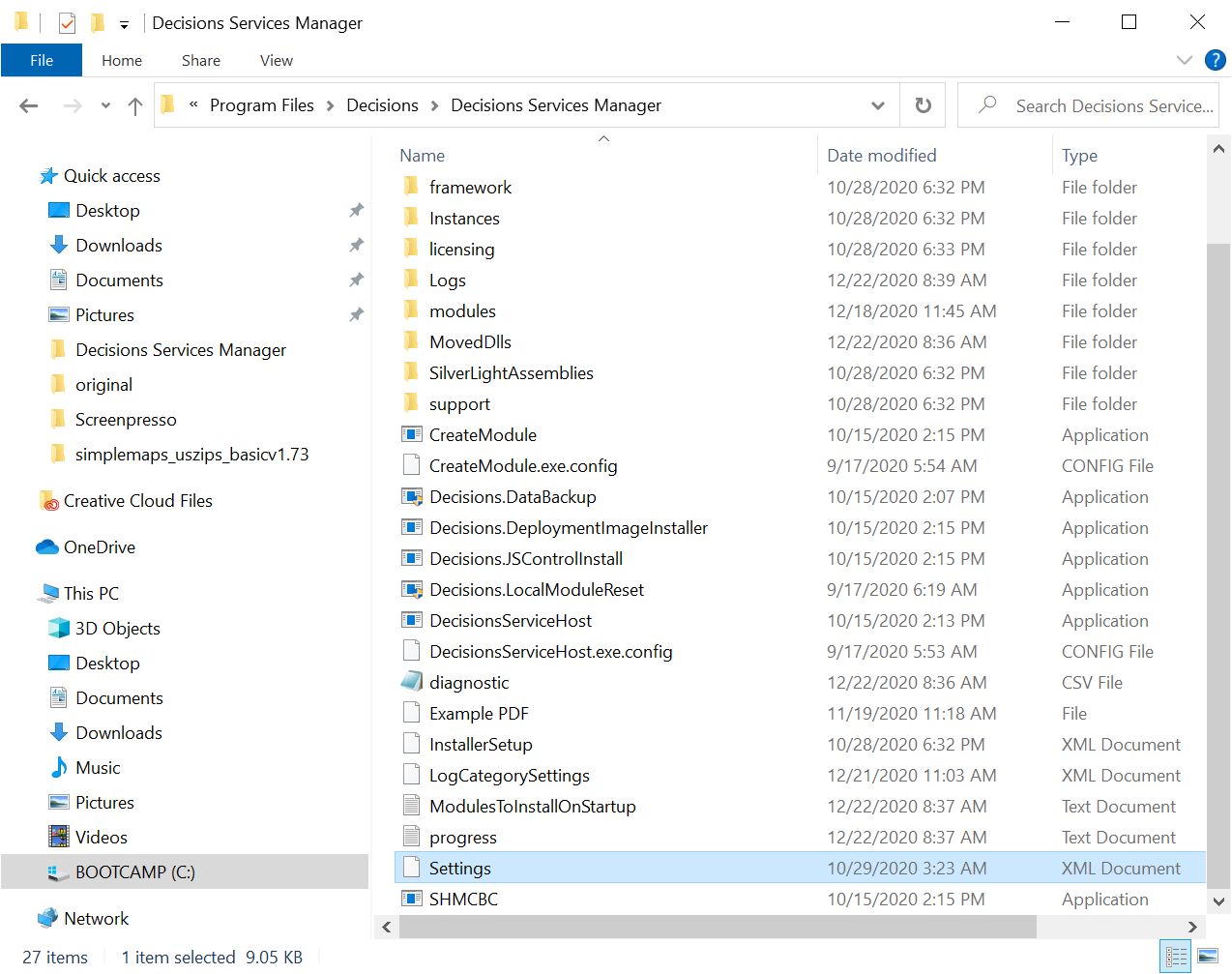
- Find the line <EnableSingleSignOn>false</EnableSingleSignOn> and set the value to true. Save changes to the file. If the line is not present, add the line to the Settings.xml file.
<EnableSingleSignOn>true</EnableSingleSignOn>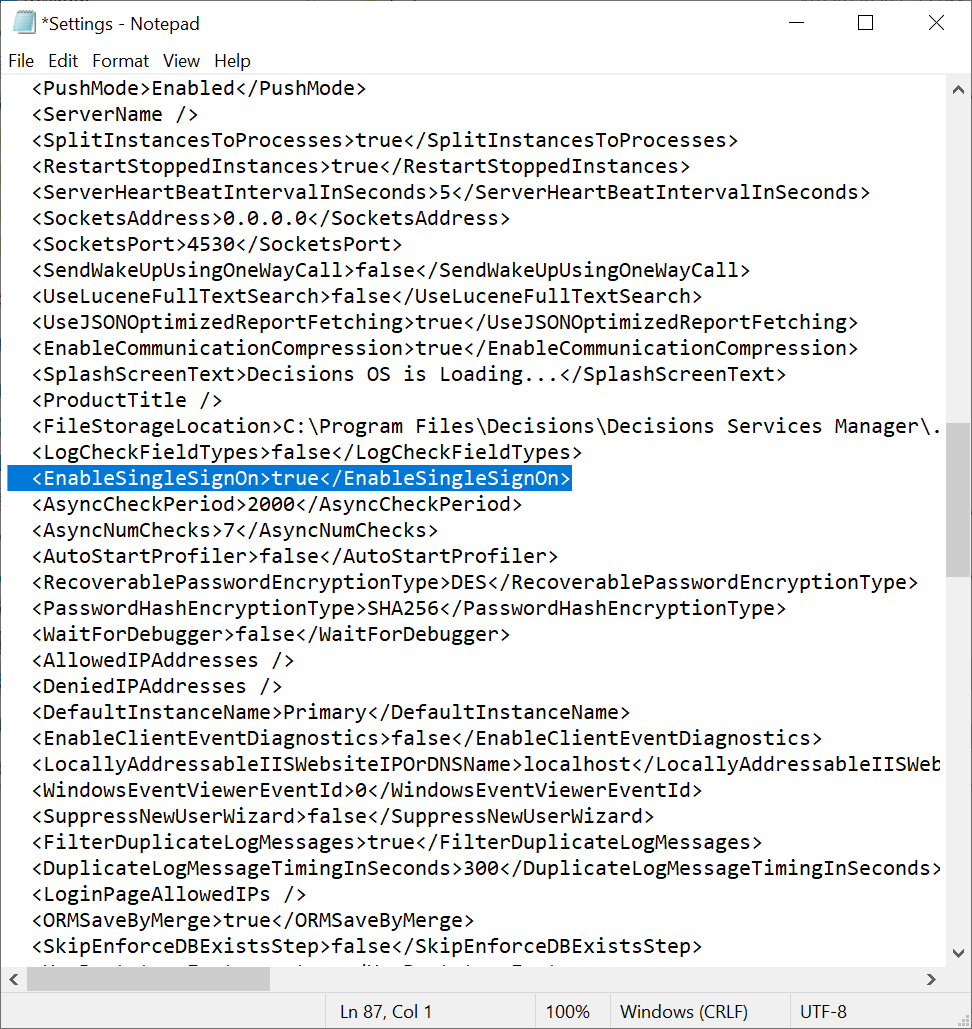
- Restart the Service Host Manager to enable SAML SSO mode.
Metadata
Replace the "http://myDecisionsServer.Decisions.com/decisions" with the URL to the Decisions installation.
Using Email Address nameId Policy
When Identity Provider is using Email Address nameId Policy, use the following code:
$metadata['http://myDecisionsServer.Decisions.com/decisions'] = array(
'AssertionConsumerService' => 'http://myDecisionsServer.Decisions.com/decisions/Primary/SAML/AssertionConsumer.ashx',
'SingleLogoutService' => 'http://myDecisionsServer.Decisions.com/decisions/Primary/logout.aspx',
'NameIDFormat' => ***'urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress'***
);
Using Transient namedId Policy
When Identity Provider is using Transient nameId Policy, use the following code:
$metadata['http://myDecisionsServer.Decisions.com/decisions'] = array(
'AssertionConsumerService' => 'http://myDecisionsServer.Decisions.com/decisions/Primary/SAML/AssertionConsumer.ashx',
'SingleLogoutService' => 'http://myDecisionsServer.Decisions.com/decisions/Primary/logout.aspx',
'NameIDFormat' => ***'urn:oasis:names:tc:SAML:2.0:nameid-format:transient'***
);
General Information
When debug logging is enabled, SAML requests and responses are logged at C:\Program Files\Decisions\Decisions Services Manager\Logs\SAML
The "AuthResponse…XML" log files will contain the certificate value that the Identity Provider server is sending back to us. This certificate needs to match the value used to configure Decisions settings.