Overview
Module Details | |
| Core Module | System -> Administration -> Features |
| Restart Required? | No |
| Steps Exposed | No |
| Step Location | Step Toolbox Breadcrumbs |
| Settings Location | System -> Settings -> OpenID Settings |
| Prerequisites |
|
OpenID Connect (OIDC) is an open standard and decentralized authentication protocol. The OpenID module allows a user to create accounts by selecting an OpenID identity provider and then use those accounts to sign on to any website which accepts OpenID authentication.
Successful implementation rests heavily on experienced client-side technical resources. Decisions' Support Team can help, but may not be able to answer questions or solve issues specific to the organization.
Version 7 Endpoints
The port number is only required if Decisions is installed on a non-standard port. This would be any port other than 80 for HTTP or 443 for HTTPS
| Endpoint | Example Endpoint |
|---|---|
| LoginURL | [base]:[port]/Account/Login |
| LogoutURL | [base]:[port]/Account/Logout |
Basic Configuration
Users cannot set up AD Sync simultaneously with Single Sign On (via SAML and OpenID Modules). Doing so will result in an error that requires users to reset their sign-on setup.
In addition, accounts that were created before the OpenID module was installed will need to be modified if they require single sign-on. Please contact Decisions Support on how to update the account
In addition, accounts that were created before the OpenID module was installed will need to be modified if they require single sign-on. Please contact Decisions Support on how to update the account
- In Decisions Studio, navigate to System > Settings. Click OpenID Settings to open the Edit Open Id Settings window. Select the Enabled checkbox and click ADD under Identity Providers.
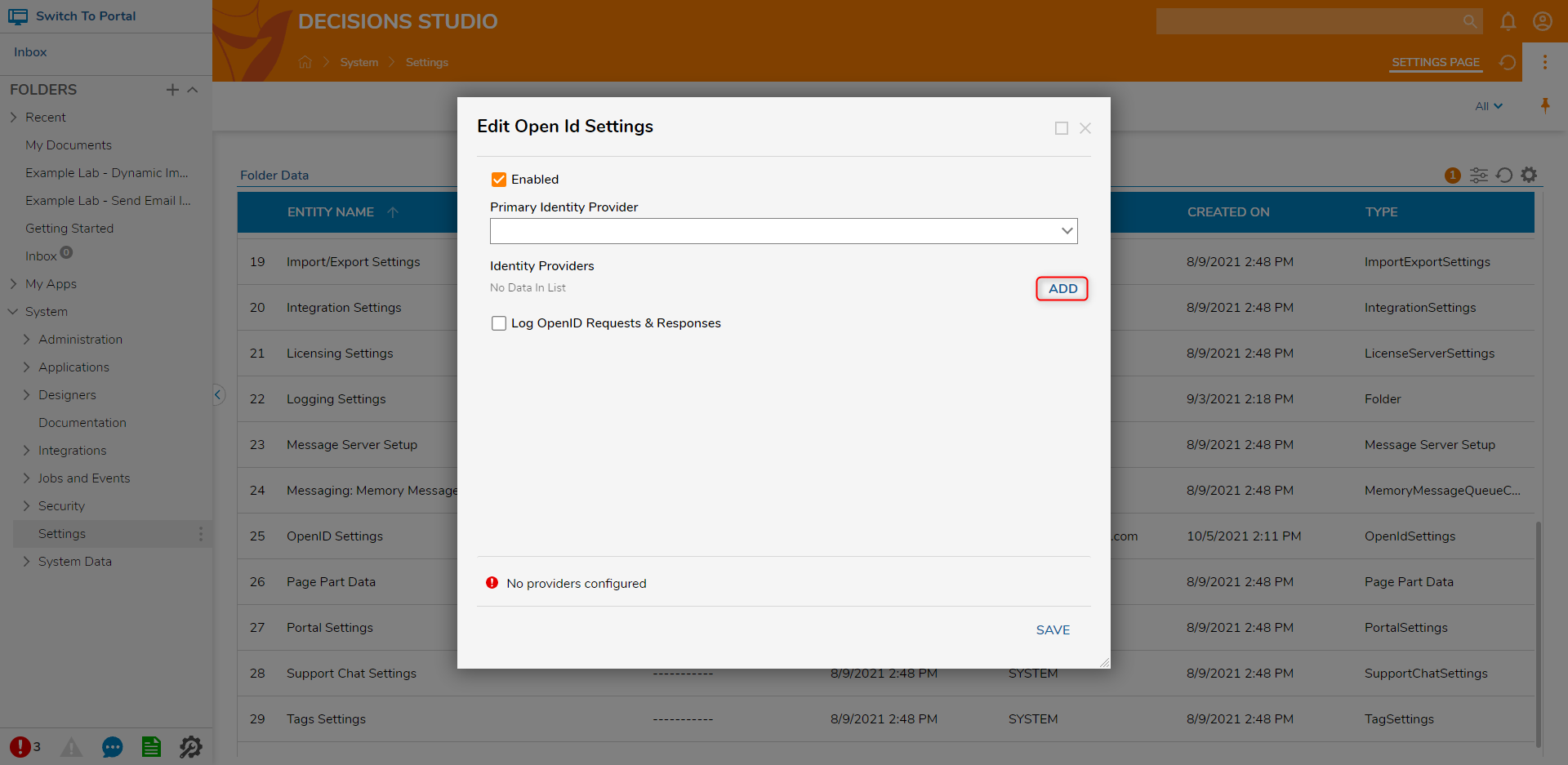
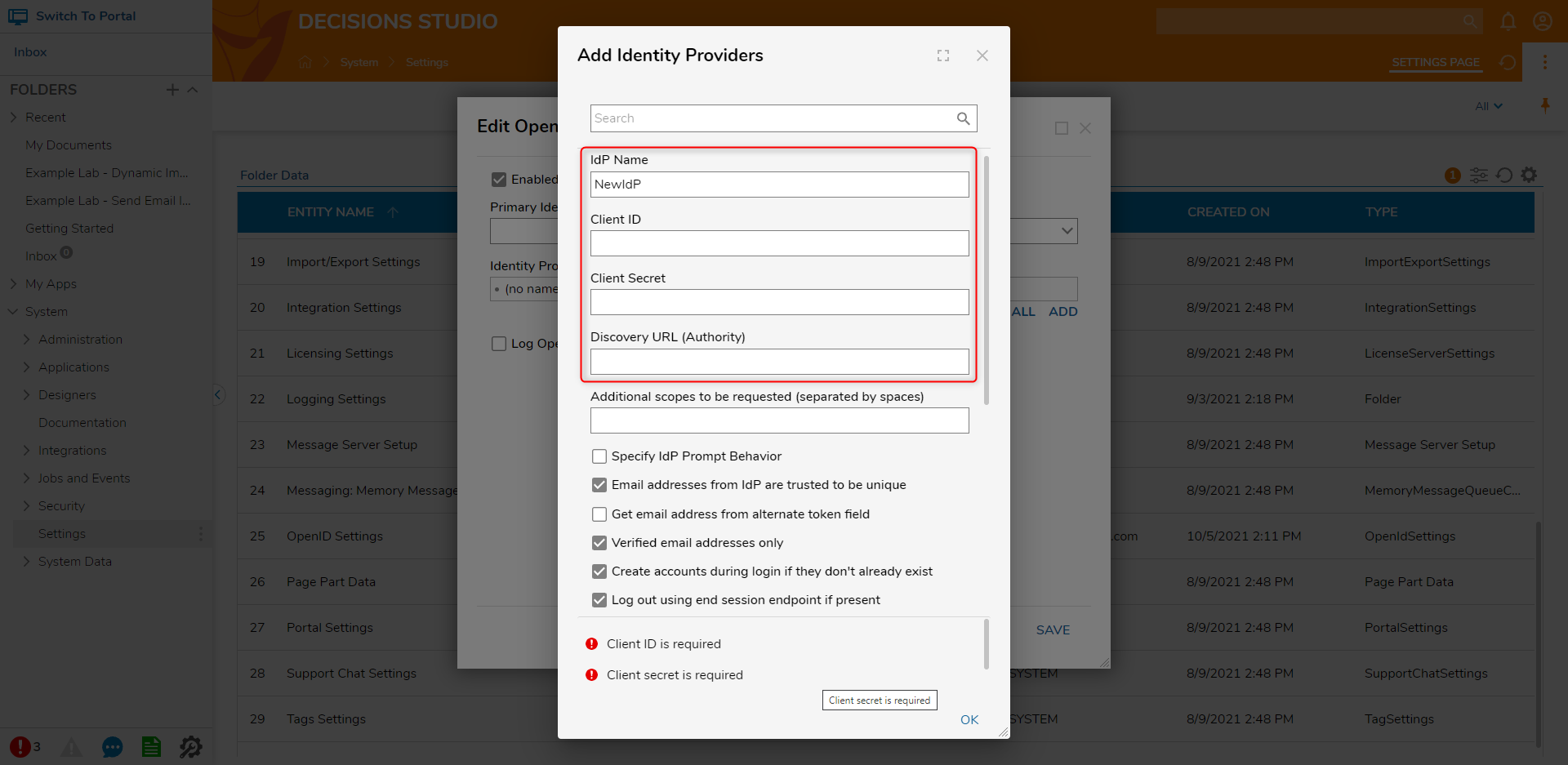
- Enter an appropriate name in the IdP Name field. The Client ID, Client Secret, and Discovery URL (Authority) fields can be obtained from an Identity Provider. The Discovery URL (Authority) usually ends with ".well-known/openid- configuration". After configuring all the appropriate fields, click OK.Be sure the information being inputted is correct. Many Identity Providers have an allowed list of redirect URIs. It may be necessary to add http://[base]:[port]/Account/Login to this list. The required information may change between different Identity Providers.
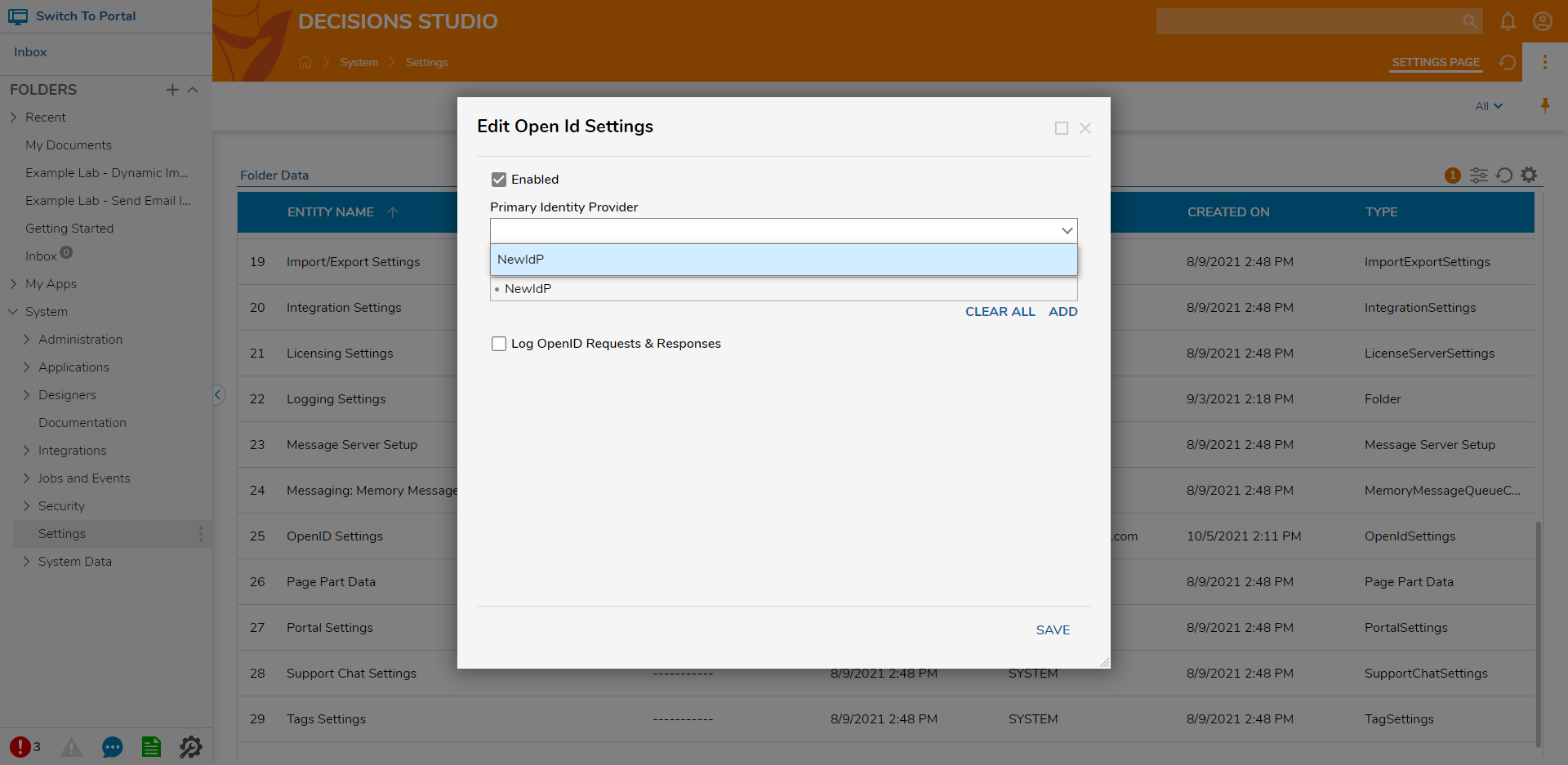
- Click the dropdown list under Primary Identity Provider and select the Identity Provider created. Click SAVE.When debug logging is enabled, requests and responses will be located at C:/Program Files/Decisions/Decisions Server/Logs/OpenID.
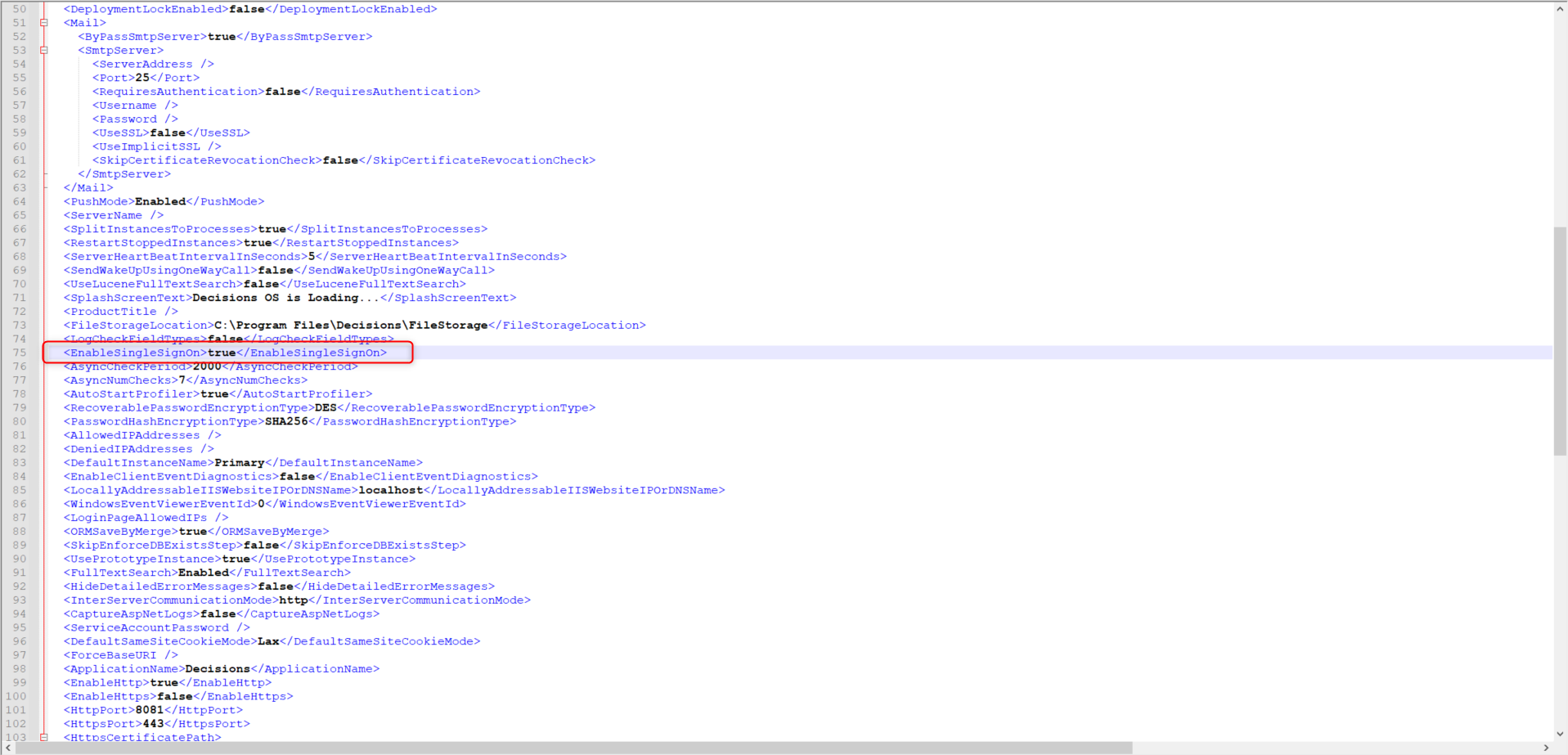
- In File Explorer, navigate to C:\Program Files\Decisions\Decisions Server and open the Settings.xml.
- Use a search tool to locate EnableSingleSignOn to true and restart the Decisions Service or IIS App Pool.
If there is an active session, it might be logged in with a non-OpenID account. Log out or start a new session to be redirected to the identity provider. Once the identity provider has accepted the credentials, it will redirect back to Decisions to log in with the OpenID account.