Account Impersonation
- 04 Nov 2021
- 1 Minute to read
- Print
- DarkLight
Account Impersonation
- Updated on 04 Nov 2021
- 1 Minute to read
- Print
- DarkLight
Article Summary
Share feedback
Thanks for sharing your feedback!
Overview
An administrator can configure accounts in a Decisions environment with account impersonation privileges. Doing this would allow account one to impersonate account two, including permission levels and access, while still using the credentials of account one. This could be helpful in a situation where a user with base-level account access has tasks that require administrator privileges. An administrator could grant access within their account settings to allow impersonation from another account in the Decisions environment, either indefinitely or for a specified amount of time.
Deactivated accounts cannot be subject to account impersonation.
Example
- Login to the Decisions environment as an administrator account.
- In the FOLDERS tree on the left, navigate to System > Security > Accounts.
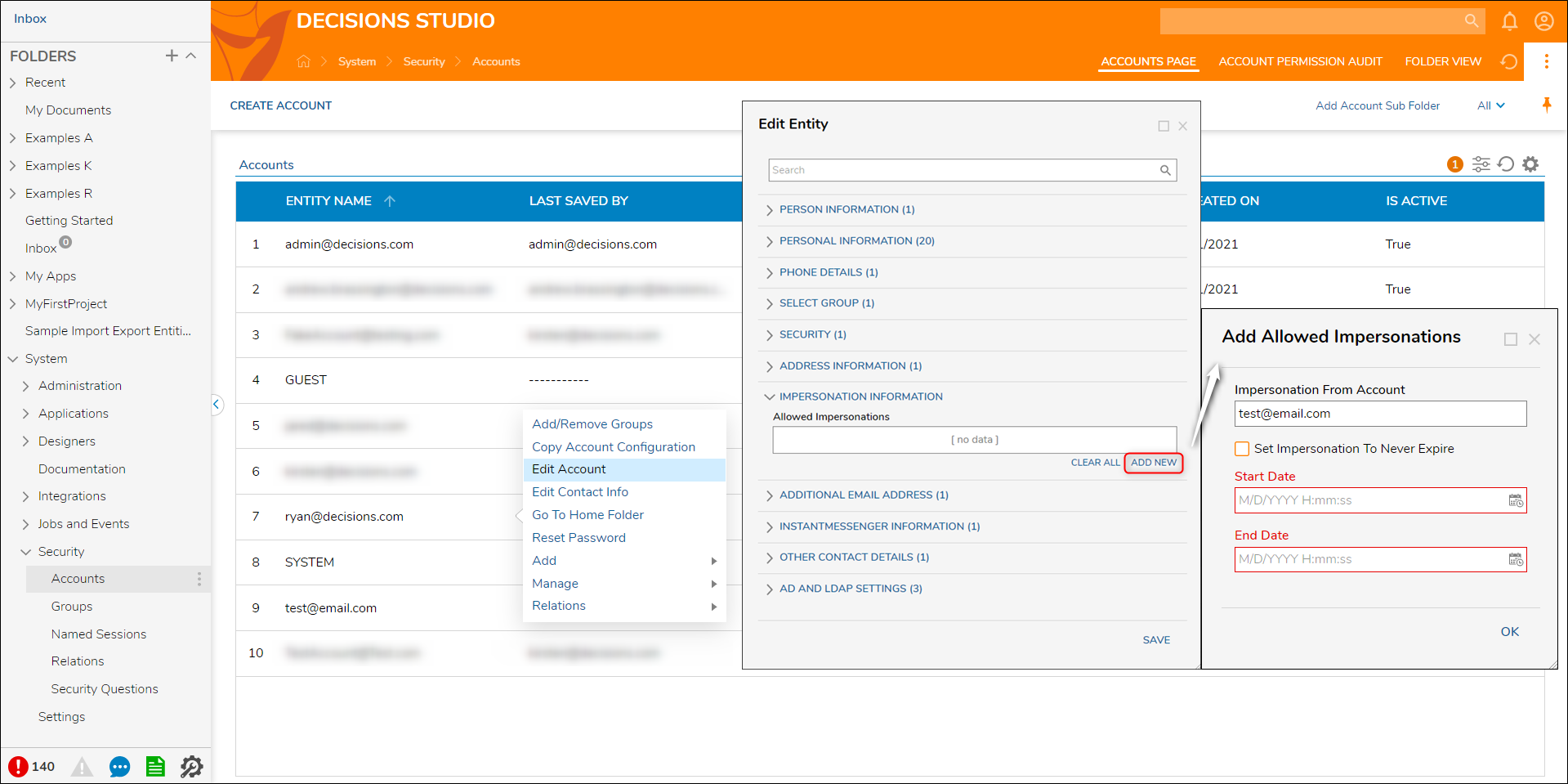
- In the Accounts list, right-click the name of the account that is going to be impersonated and select Edit Account from the Action Menu.
- When the Edit Entity window appears, find the IMPERSONATION INFORMATION section.
- Under the Allowed Impersonations box, select ADD NEW.
- When the Add Allowed Impersonation window appears, enter the email address of the impersonating account in the Impersonation From Account box.
- Use the Set Impersonation To Never Expire to allow indefinite impersonation access.
- Use the Start Date/End Date pickers to specify a timeframe with which the account will be allowed impersonation access.
- Save the settings once complete and logout of the Decisions environment as the administrator account.
- Login to the Decisions environment with the base-level account that was granted impersonation access.
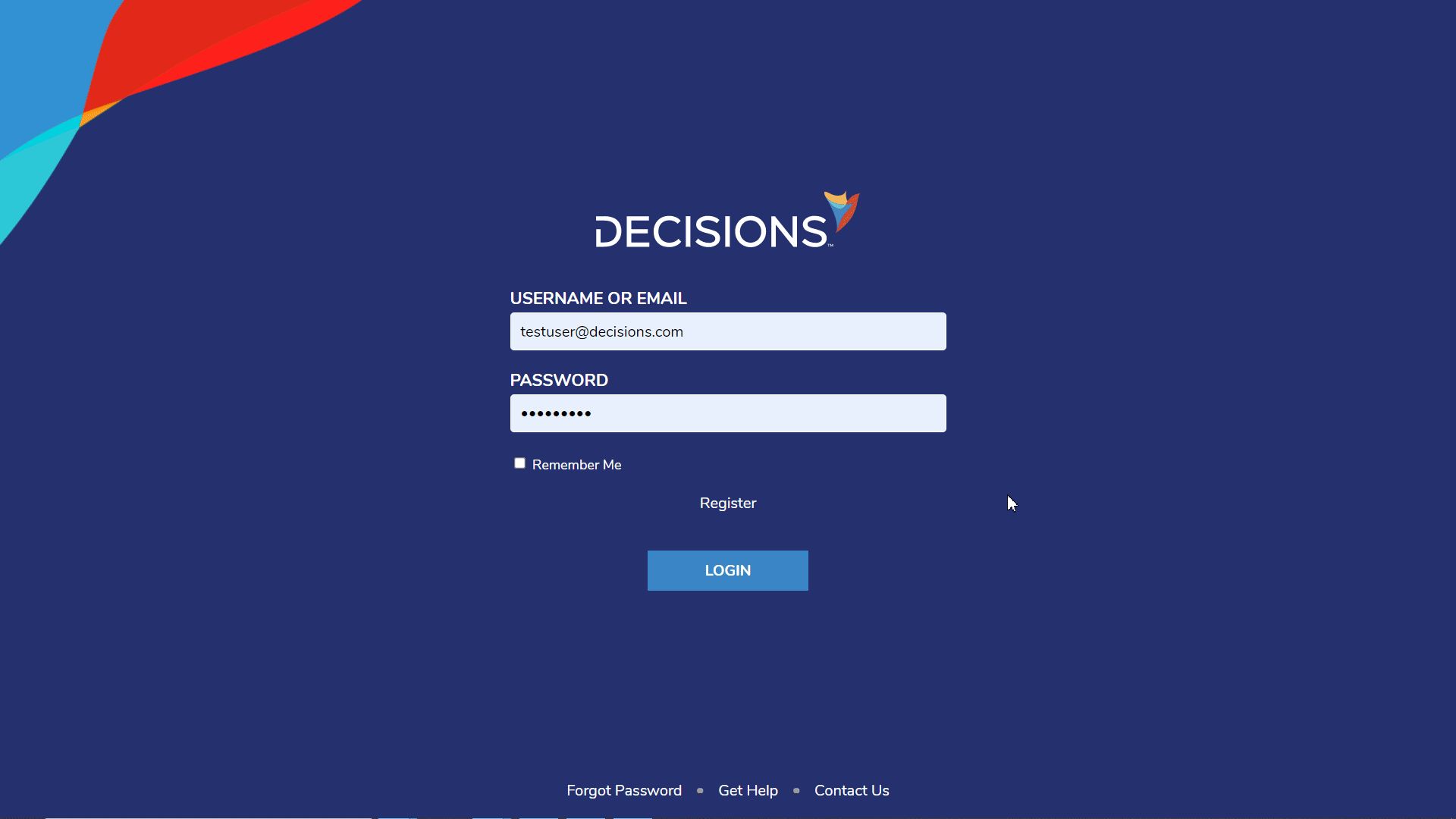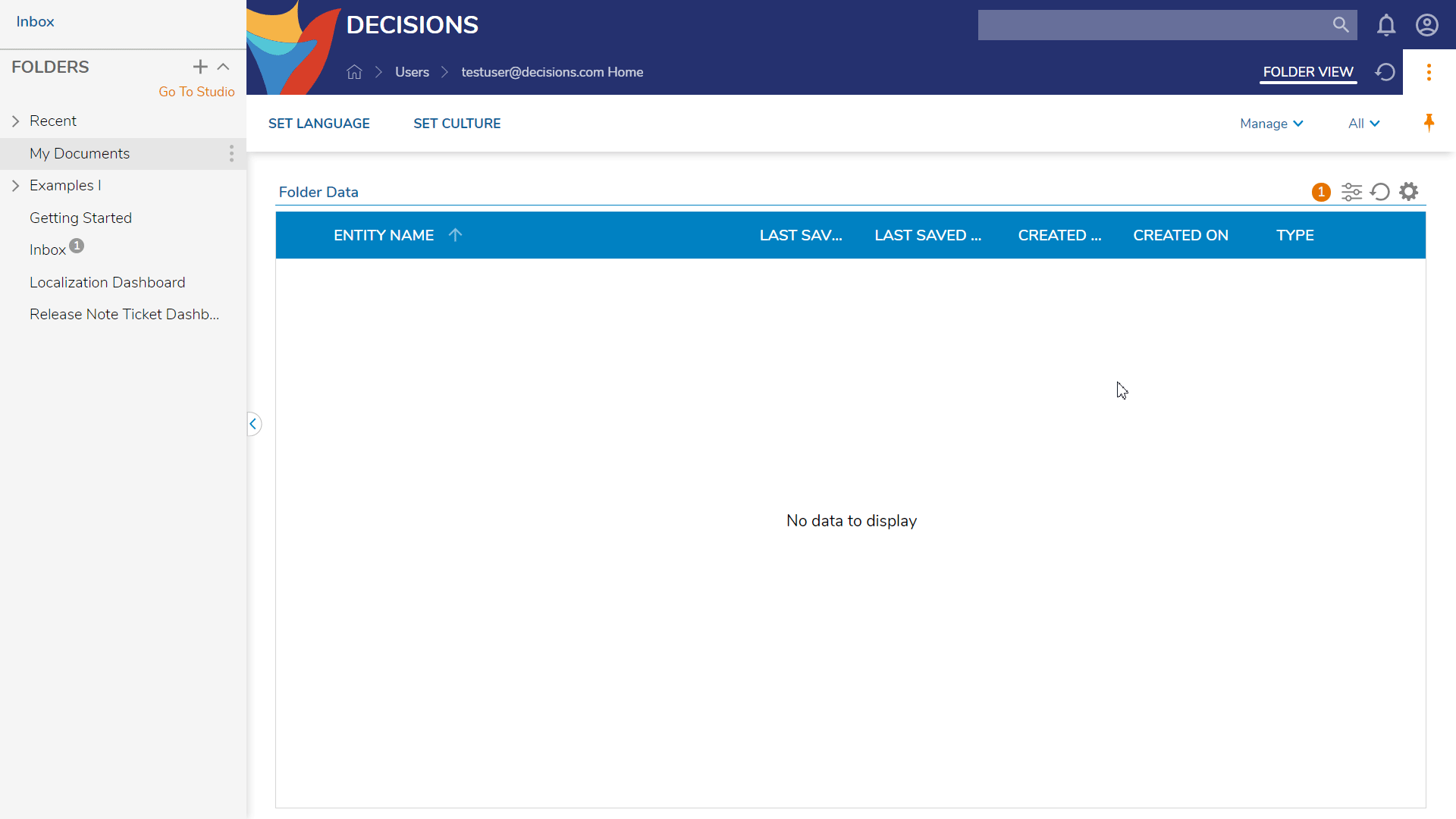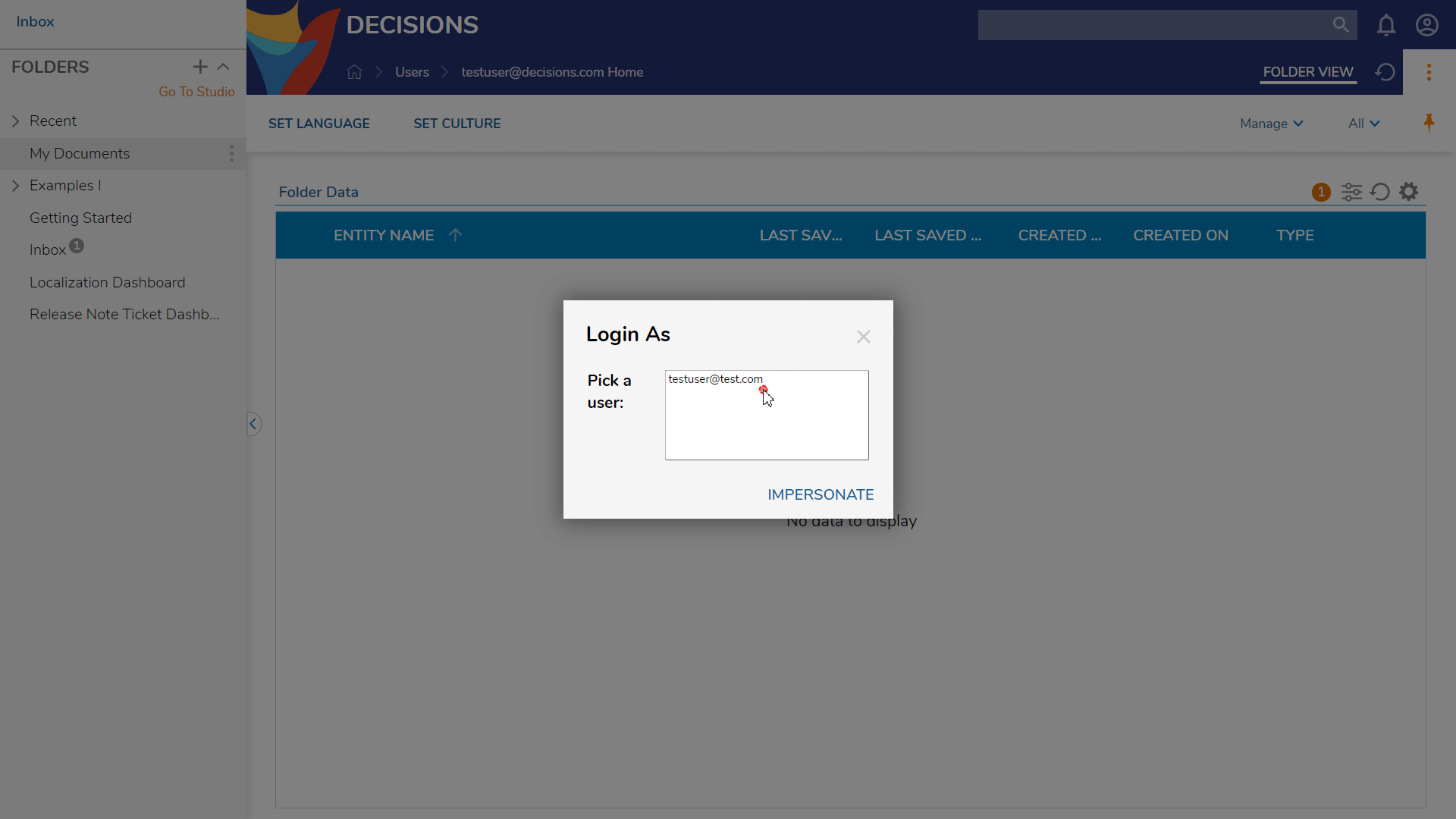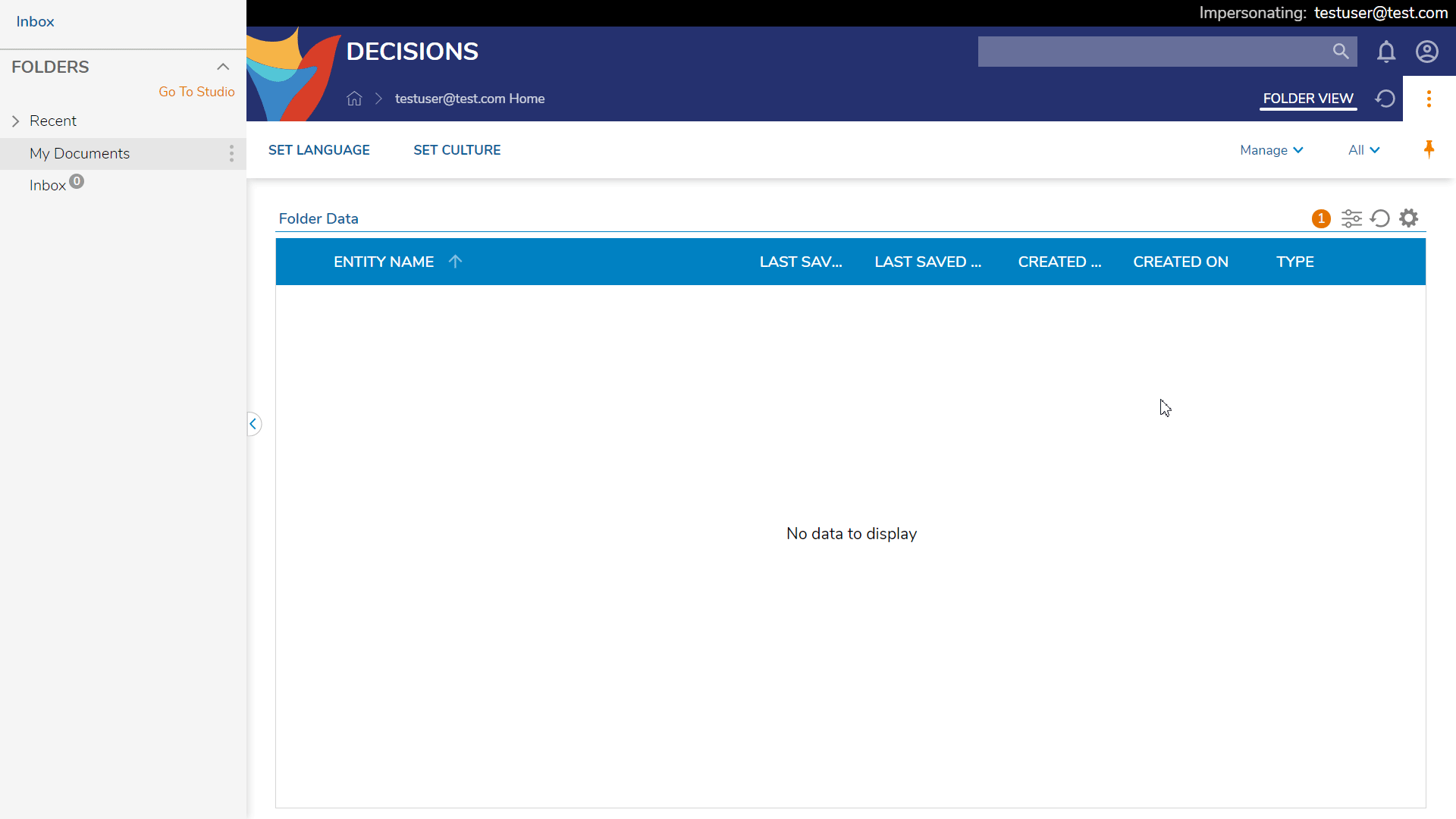
- Select the Person icon in the top-right corner of the Portal and choose Login As... from the menu.
- When the window appears, select which account should be impersonated (based on the configurations made in the previous steps) and select IMPERSONATE.
- After the interface refreshes, a black bar will appear at the top of the environment to signify which account the user is impersonating. At this point, granted permissions will be accessible in the environment.
Was this article helpful?



