Single Logout with SAML
- 21 Feb 2023
- 2 Minutes to read
- Print
- DarkLight
Single Logout with SAML
- Updated on 21 Feb 2023
- 2 Minutes to read
- Print
- DarkLight
Article Summary
Share feedback
Thanks for sharing your feedback!
Overall
Configuring Single Log Out (SLO) involves details that vary based on the provider and customer environment, these settings are strict and must be performed by a knowledgeable administrator configuring the connection. An administrator with experience in SLO or the IT infrastructure of the organization can help streamline the process. The Decisions Support team is available to help, but may not be able to answer questions or solve problems that are unique to a customer organization.
Requirements
- SAML Module installed with EnableSingleSignOn set to ‘true’. To learn how to install a module, see Installing Modules.
- PFX certificate for signing requests and password. To learn about generating a certificate, see Generating Certificates with OpenSSL.
- Generated metadata for Decisions (most IdPs support this, but users may need to manually enter these values. To generate metadata, go to https://www.samltool.com/sp_metadata.php
- Admin access to the IdP that will be configured and connected to.
If auditing options are enabled, a Session Expired Logout audit message will be displayed for log-offs for expired sessions.
Example
This example will demonstrate how to set up and configure Single Logout using SAML.
- Load the PFX certificate onto the filesystem that Decisions is running off of.The certificate does not need to be installed, just added to the system.
- Generate metadata by going to https://www.samltool.com/sp_metadata.php and using the form. Then, click BUILD SP METADATA.
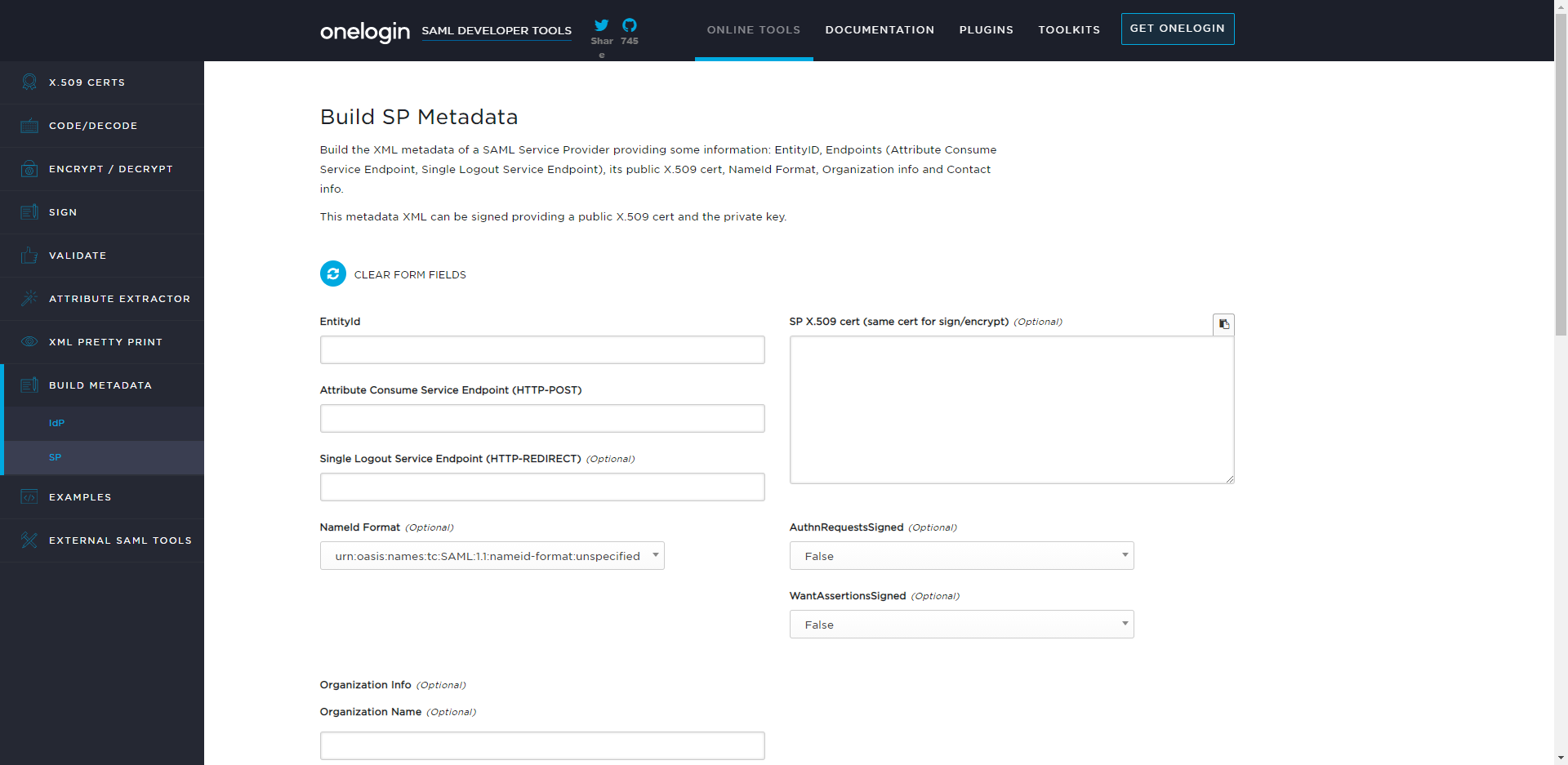
- Fill out the following fields: Endpoint PortsPort numbers are online needed if installation is to a non-standard port (80 for http, or 443 for https).
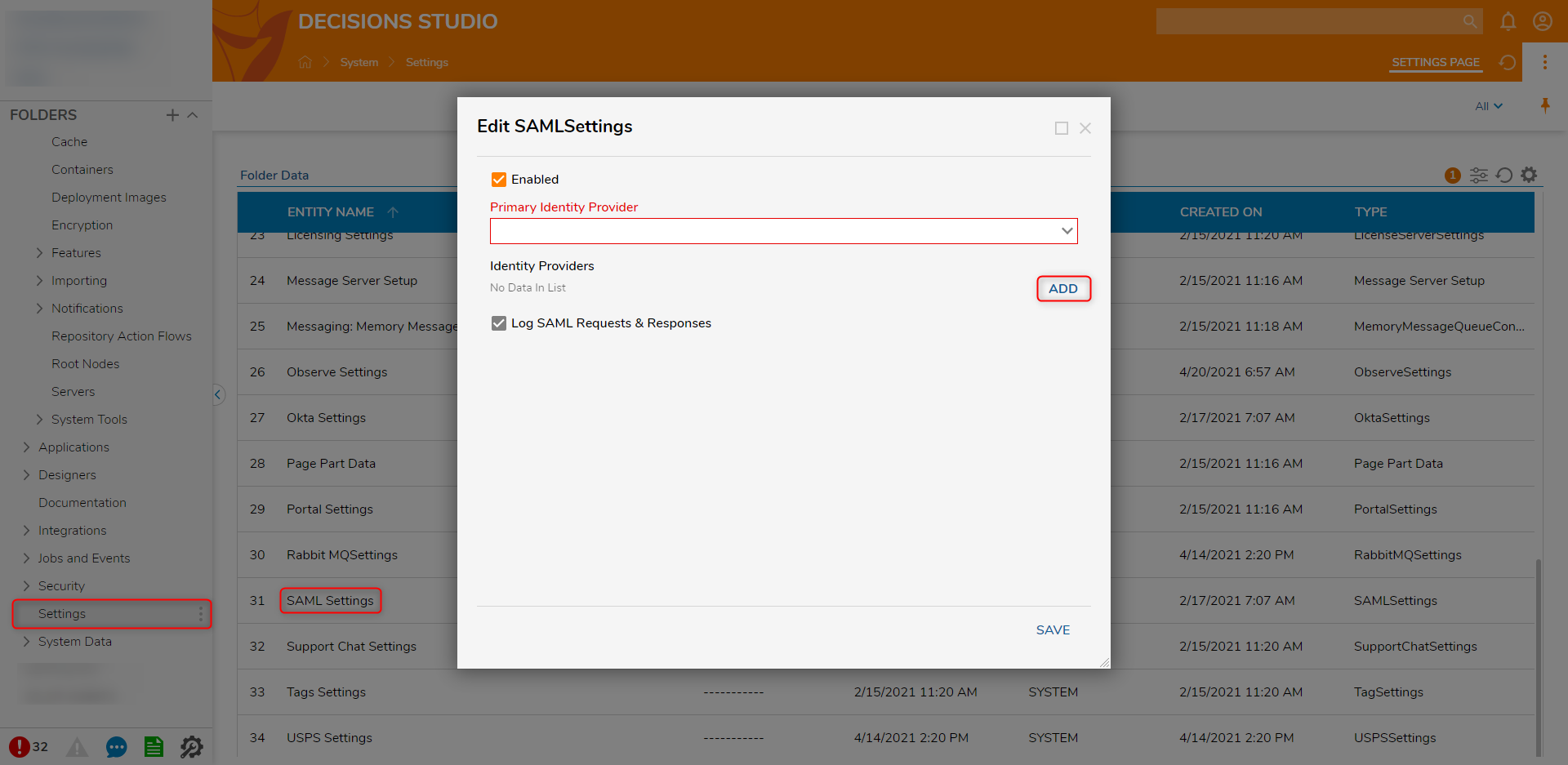
Field Name Description EntityID Same value as the SP Issuer/EntityID in the SAML module Attribute Consume Service Endpoint Decisions SAML Handler: [base]:[port]/SAML/AssertionConsumer Single Logout Service Endpoint Decisions Logout Handler: [base]:[port]/Account/Logout NameID Format Needs to match the nameID format of IdP being used. Found in the IdP settings but users can also get an AuthResponse (from a successful login) using the Log SAML Requests and Responses checkbox in the SAMLSettings window. SP X.509 cert Can be left blank AuthnRequestsSigned Determined by IdP, but most likely will be False WantAssertionsSigned Determined by IdP, but most likely will be False - Navigate to System > Settings and click SAML Settings. Click ADD under Identity Providers to create a new Identity Provider.
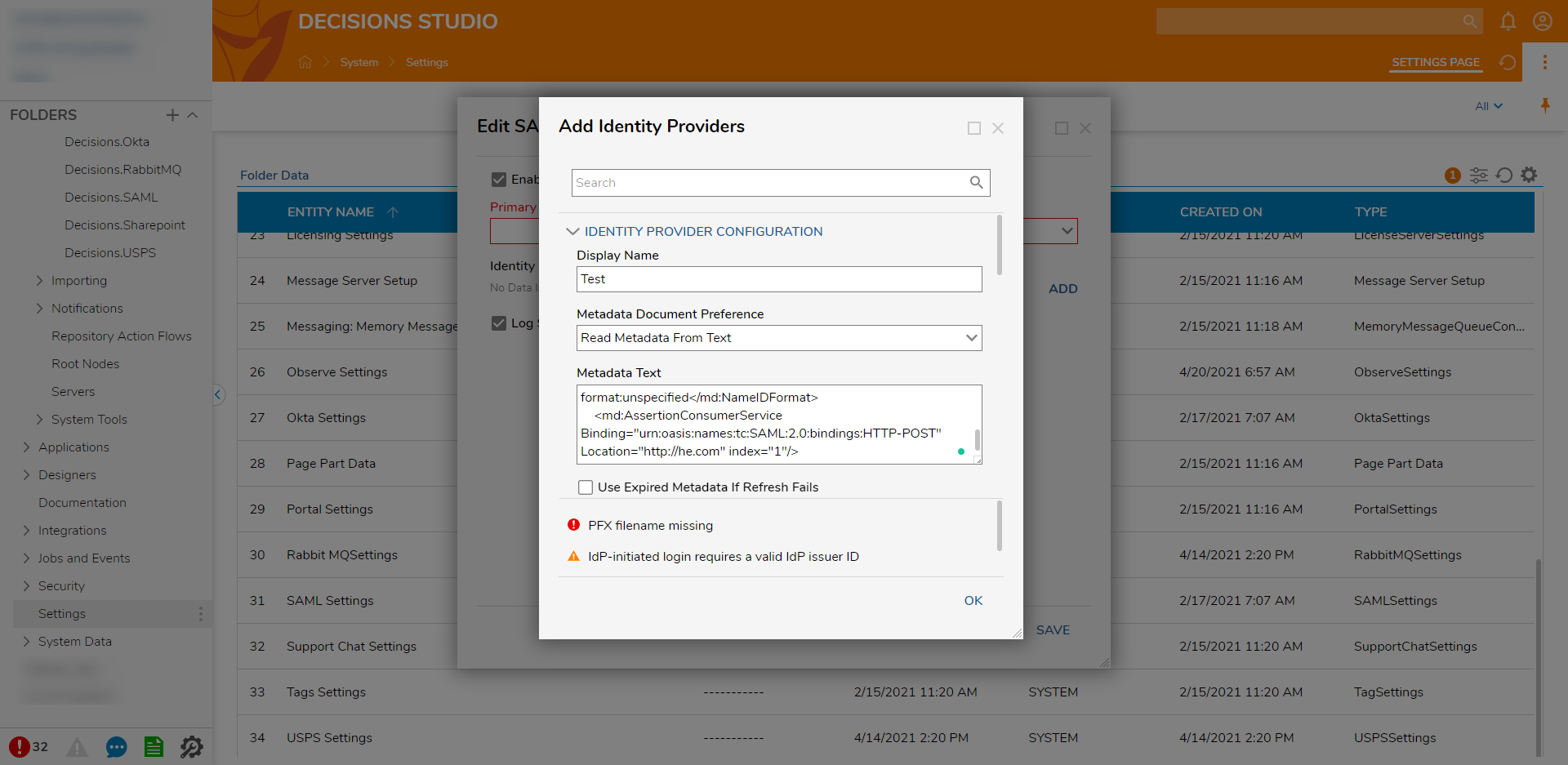
- Click the dropdown list under Metadata Document Preference and select Read Metadata From Text. Then, copy and paste in the generated metadata.
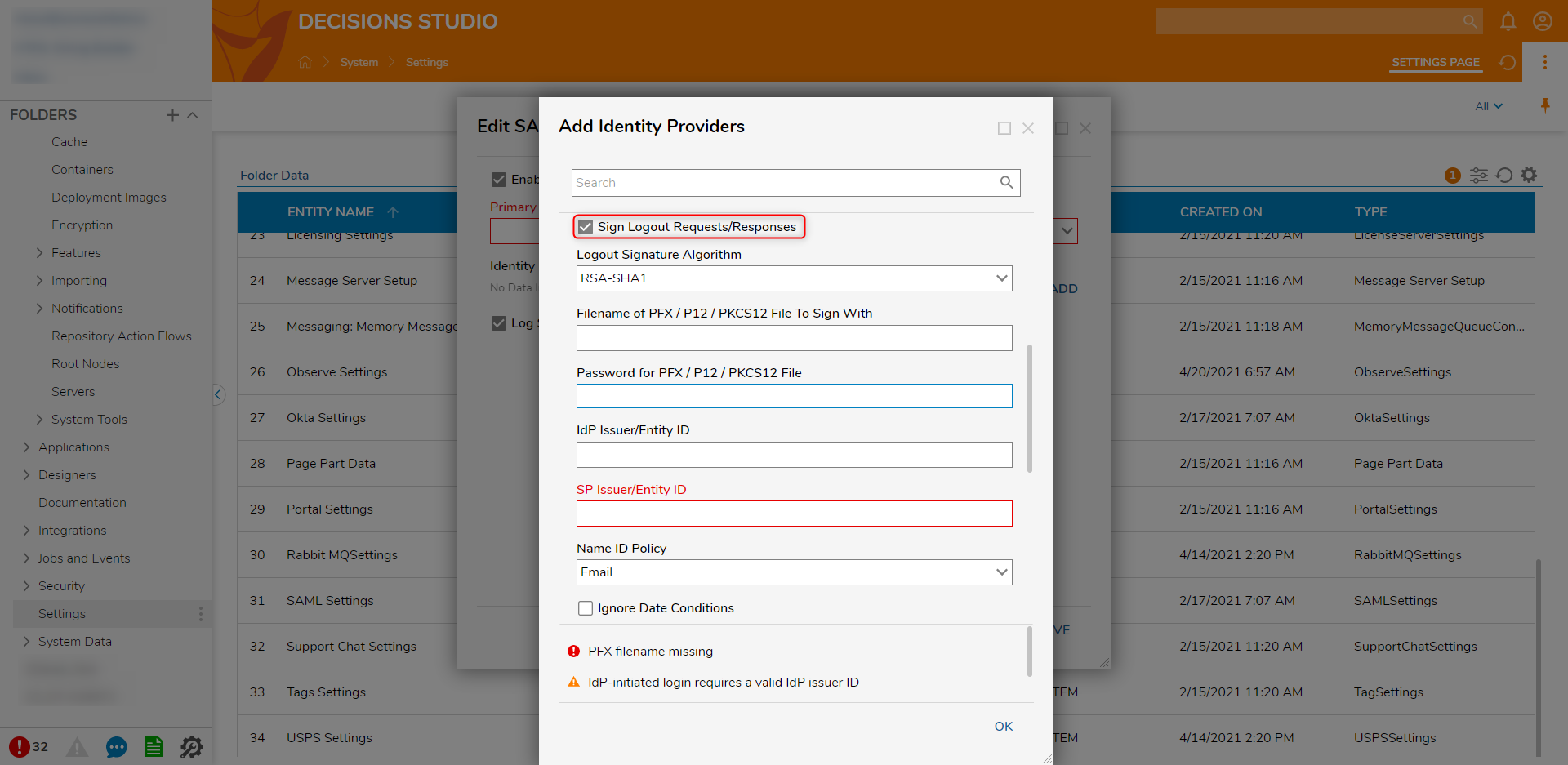
- Click the checkbox next to Sign Logout Requests/Responses. Paste the file path of the PFX certificate in the Filename of PFX / P12 / PKCS12 File To Sign With field and the password (if any) in the Password for PFX / P12 / PKCS12 File field.If the value for LogoutURL is blank after inputting the above information, regenerate the metadata or enter the IdP's SLO URL. Many providers support a Post Logout Redirect URL. A common practice is redirecting to the Decisions Login page using the Portal Base URL.
- After configuring all other required fields, click OK. Then, click SAVE on the Edit SAMLSettings window.
Was this article helpful?





