Overview
The most common use case of the Decisions API is running Rules and Flows through a Rest Service call. However, the API can be used for other functions such as provisioning users, setting up folders or projects, setting branding, and more.
Authenticating to Decisions API
There are two primary ways to authenticate to Decisions API; using the authentication information provided by the View Integration Details page or providing authentication information in the HTTP Header.
Authentication information is required to call Decisions via API. This allows Decisions to grant access, check authorizations for specific activities, govern access to specific data, and audit the actions taken in the product.
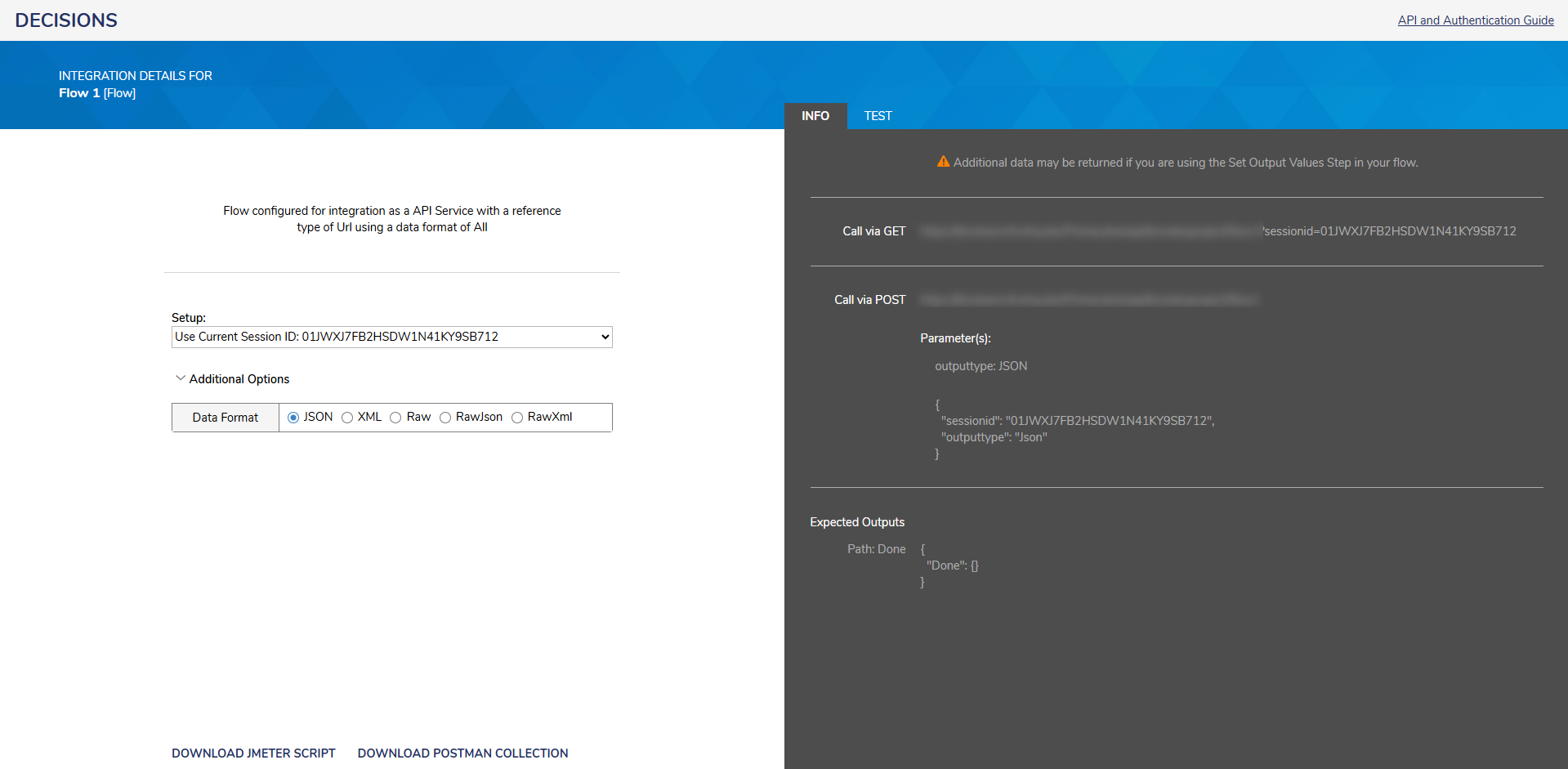
View Integrations Details Page
The View Integrations Details page allows users to set parameters and obtain the appropriate GET or POST request types to execute a task.
| Request Type | Description |
|---|---|
| GET | Authentication information is provided in the request URL |
| POST | Authentication information is included as part of the POST body |
Request Header Authentication
Users have the option to add authentication information in the Request Header. By using this option, users do not need to provide the authentication information in the URL or POST body. Instead, provide the information in the Request Header's Authorization field option.
The Header values for the request will be different based on the type of authorization type.
| Authorization Type | Input Passed | Example Header |
|---|---|---|
| Basic | Username and Password encoded string (Base 64 Encode of "username:password", e.g., Base 64 encode of 'admin@decisions.com:admin') combined with a colon character | "Authorization":"Basic YWRtaW5AZGVjaXNpb25zLmNvbTphZG1pbg==" |
| Session | SessionID or NamedSessionID | "Authorization":"SessionID {SessionID or Named Session ID}" |
| Bearer | JWT Token | "Authorization":"Bearer {JWTTOKEN}" |
Basic Authorization Type
Username and Password are passed to the services as a Basic Authorization and should only be used for simple, periodic API calls. In most API uses, the username and password are used to create a Session for subsequent calls.
To programmatically send the User id and Password, combine them with a colon (:) character and then base64 encode the result. This is placed in the Header with the ‘Basic’ keyword.
string merged = $"{userName}:{userPassword}";
string toSend = Convert.ToBase64String(System.Text.Encoding.UTF8.GetBytes(merged));
HttpClient client = new HttpClient();
client.DefaultRequestHeaders.Authorization = new System.Net.Http.Headers.AuthenticationHeaderValue("Basic", toSend));
client.GetAsync(“http://localhost:8081/Primary/restapi/Flow/2474ea6a-5472-11ec-8c48-803253078da6?”);
.png)
Session Authorization Type
A SessionID will be returned by utilizing the following API call.
URL:"http://[baseportalURL]/Primary/REST/AccountService/LoginUser"
Post Body: { "outputtype" : "Json" }
Http Header: Authorization: Basic (Base64 String as described above)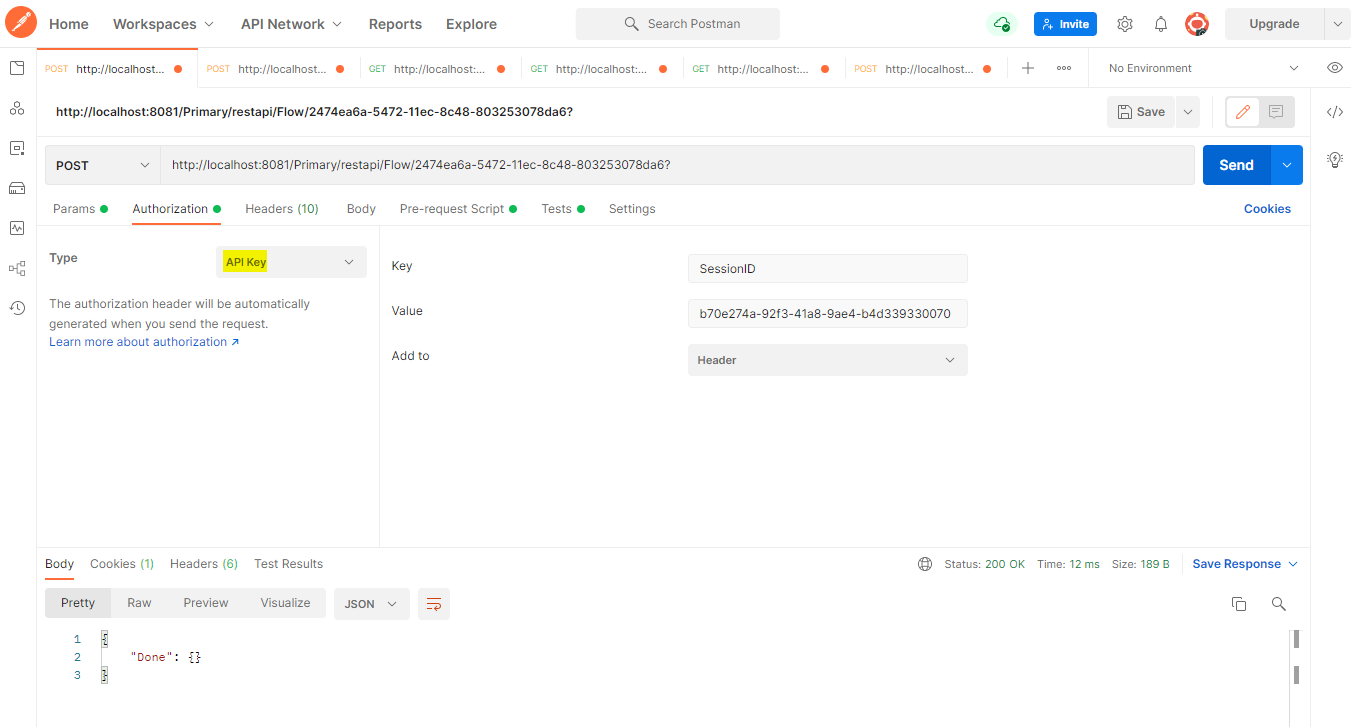
JWT Authorization Type
Authorization using Decisions Native JWT
To configure and use a Decisions native JWT, refer to the article How to Set Up and Use JWT.
Authorization using External OAuth JWT
Note: This feature is available only in v9.7 and above.
The Platform supports JWT (JSON Web Token)-based authentication for secure API access. This allows external applications to authenticate and interact with Decisions APIs using JWTs issued by their own Identity Provider (IdP).
Users must configure JWT Access on the platform at System > Security > JWT Access. The following table provides more detailed information on each setting.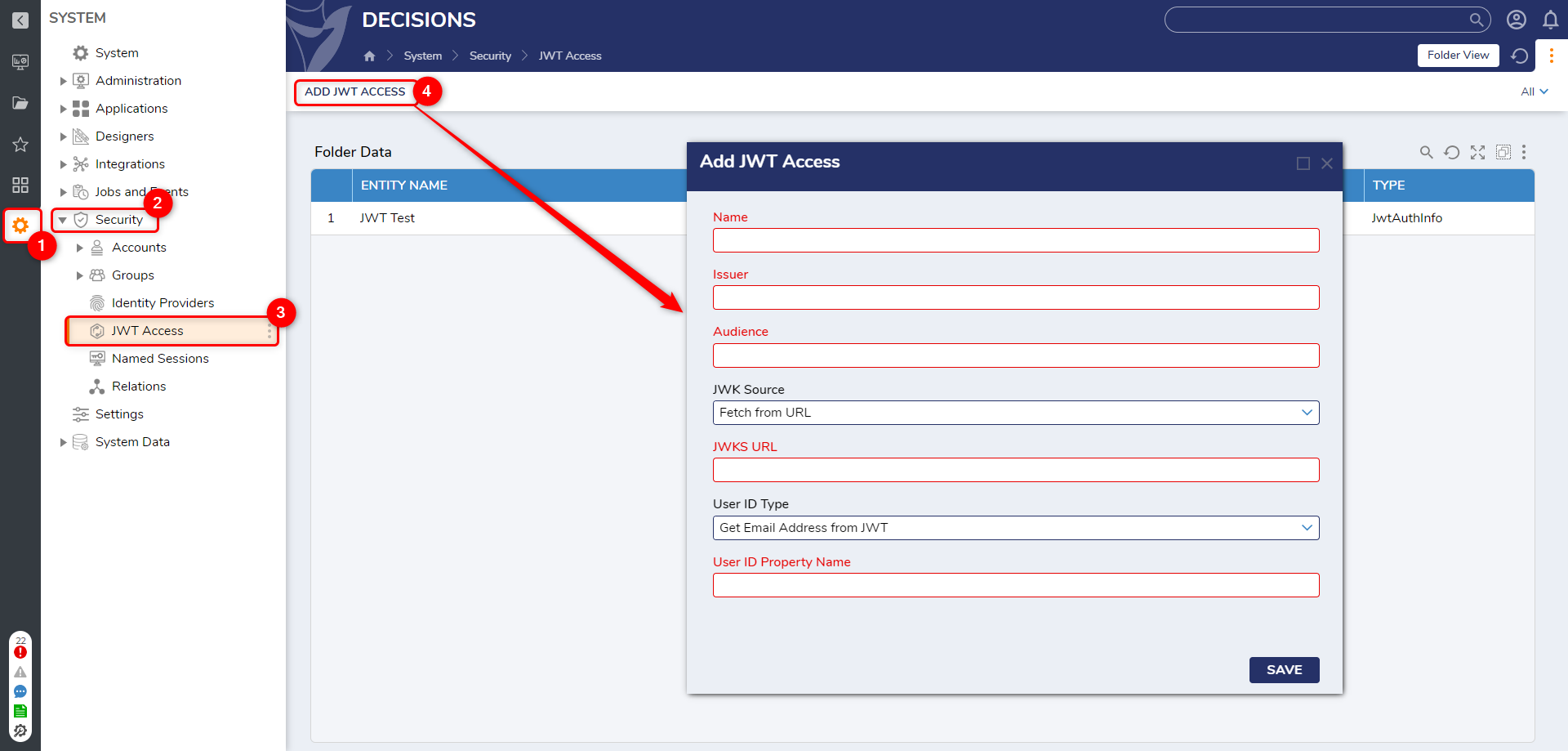
| Setting Name | Description |
|---|---|
| Name | A user-defined name to create an entity |
| Issuer(iss) | This specifies the expected issuer of the JWT, such as https://auth.example.com. This ensures that only tokens issued by the trusted IdP are accepted, preventing unauthorized tokens from being used in API requests. |
| Audience (aud) | This defines the expected audience value in the JWT. This guarantees that the token is issued specifically for the Decisions API, preventing its misuse by other applications. If the audience claim in the token does not match the configured value, authentication will fail. |
| JWK Source | This defines how Decisions retrieves the JSON Web Key (JWK) for token validation. The JWK contains the cryptographic keys used to verify the JWT signature.
|
| User ID Type | This determines how Decisions identifies users from the JWT for authentication and authorization:
|
Once the JWT token has been acquired, API calls can be achieved by using the Bearer Authorization Type.
URL: http://[portalbaseURL]/Primary/?[DesignerElement]ID=[DesignerElementIDValue]&Action=api&outputtype=JSON
Http Header: Authorization: Bearer (JWT token)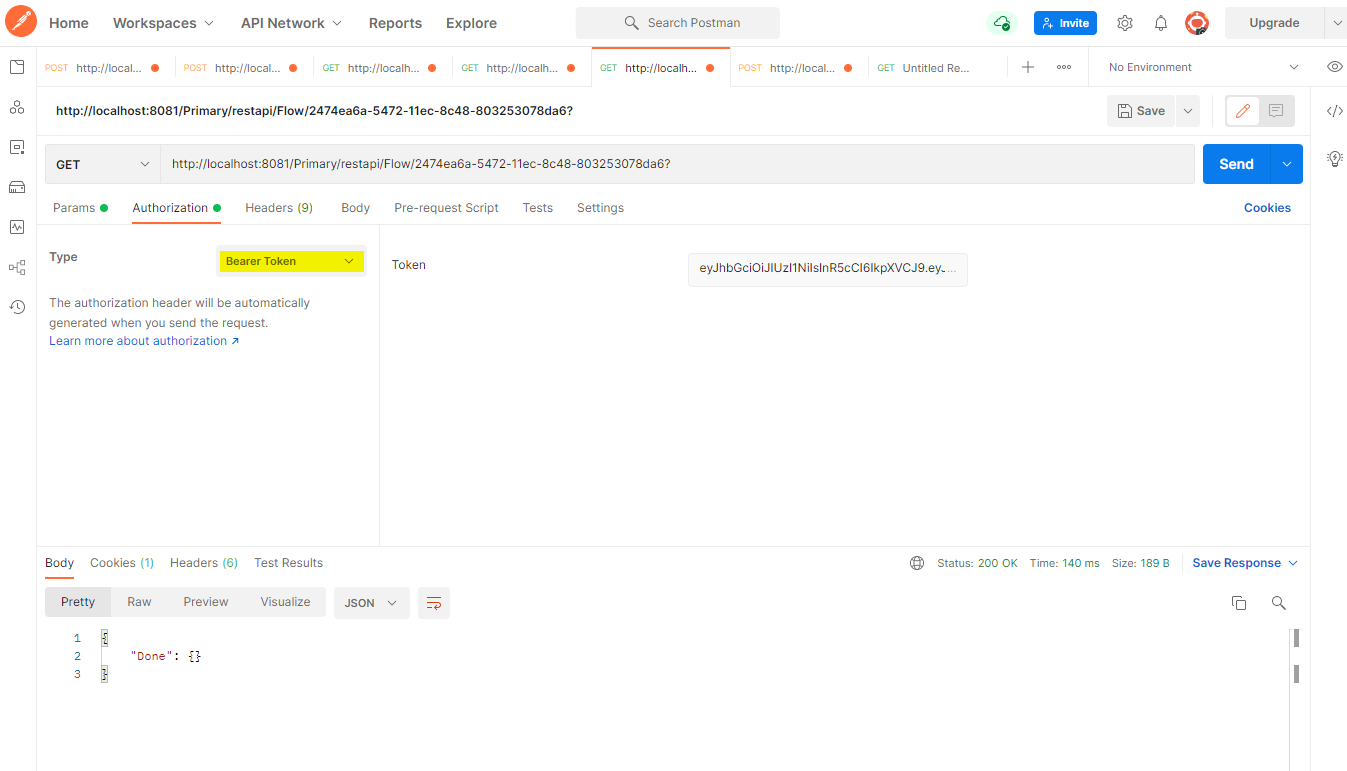
Request Cookies on API Calls
On API calls, Decisions uses the following headers and cookies:
| Cookie Name | Description |
|---|---|
| Decisions.Auth | Allows a user to stay logged in after authentication |
| SessionValue | Passed in on calls to connect actions to an account |
| ClientEventSessionId | Unique ID to each open tab of Decisions (not the same as the SessionID) |
| formSessionInfoId | ID related to the currently running Form |
Feature Changes
| Description | Version | Release Date | Developer Task |
|---|---|---|---|
| Added the ability to call the Decisions APIs using OAuth JWT. | 9.7 | February 2025 | [DT-042083] |
| Changes to default JWT. | 9.10 | May 2025 | [DT-044294] |