Overview
Configuring Single Log Out (SLO) ensures seamless user experiences within authentication systems. SLO intricacies are contingent upon the characteristics of both the identity provider and the customer's operational environment. The responsibility of handling SLO configuration often falls upon administrators who understand SLO protocols, authentication mechanisms, and the intricacies of the organization's IT infrastructure. Administrators experienced in SLO procedures or well-acquainted with the organization's technological landscape are best suited to execute this process.
While the Decisions Support team is available to provide guidance and assistance throughout the SLO configuration, it's important to recognize that certain challenges or queries might be uniquely tied to the intricacies of a particular customer's setup. As such, the team can offer invaluable general insights; specific issues stemming from the customer's organizational context may require custom solutions.
Customers will need to generate their own certificates. Decisions does not provide certificates for signing requests to Identity Providers for security reasons.
Prerequisites
- SAML Module Installation: The SAML module must be installed, and the 'EnableSingleSignOn' parameter should be set to 'true'.
- PFX Certificate for Signing: A PFX certificate is required for signing requests. Ensure you have a valid PFX certificate along with its associated password. To generate a suitable certificate, consult the guidelines for Generating Certificates using OpenSSL.
- Generated Metadata: While most IdPs support using metadata, it might be necessary to input specific values manually. Generate the required metadata.
- Administrative Access to IdP: You must have administrative access to the IdP that you intend to configure and establish a connection with.
Example
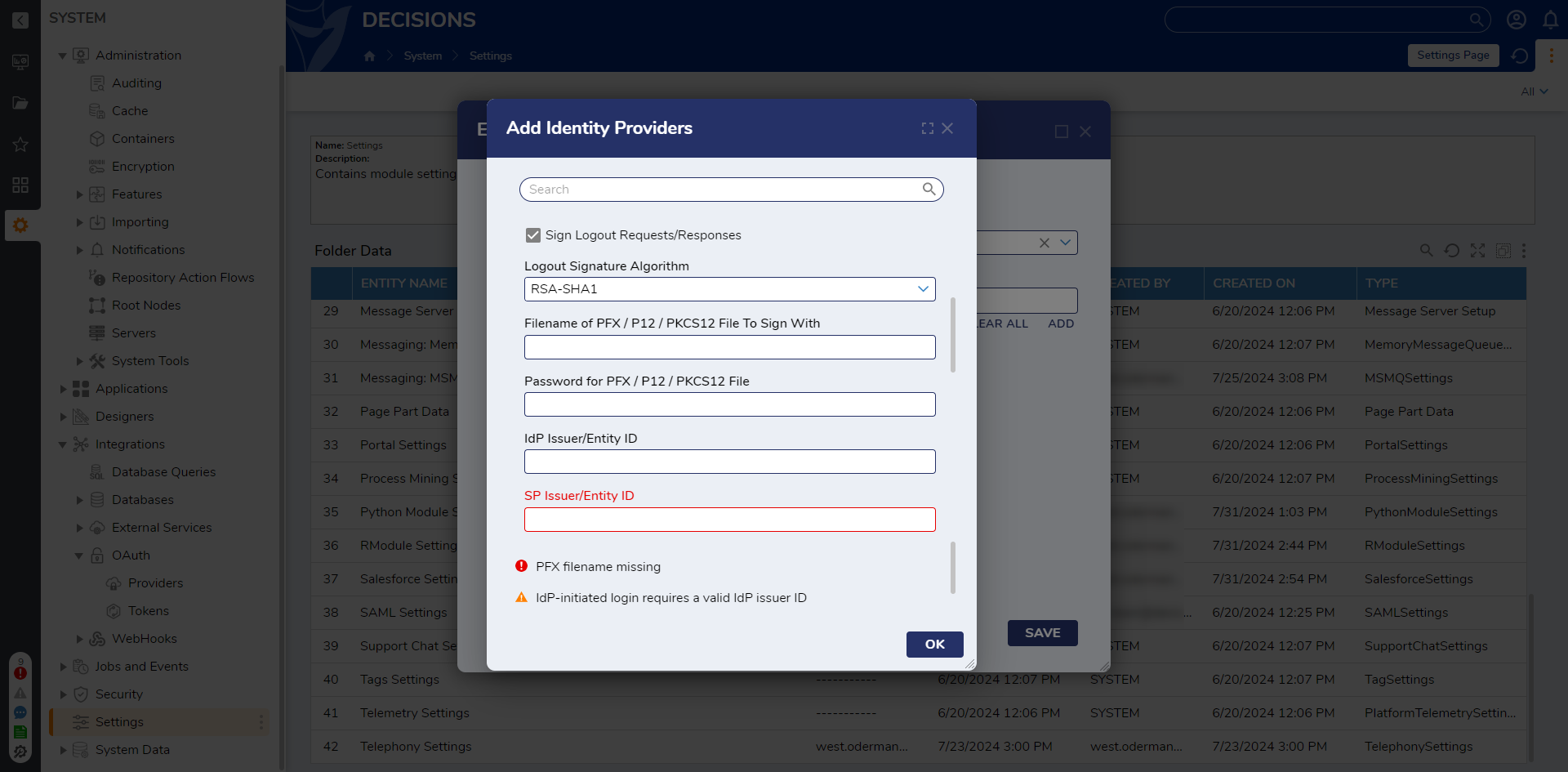
- Within the SAML Settings > Identity Providers dialog, click the checkbox next to Sign Logout Requests/Responses. Paste the file path of the PFX certificate in the Filename of PFX / P12 / PKCS12 File To Sign With field and the password (if any) in the Password for PFX / P12 / PKCS12 File field.If the value for LogoutURL is blank after inputting the above information, regenerate the metadata or enter the IdP's SLO URL. Many providers support a Post Logout Redirect URL. A common practice is redirecting back to the Decisions Login page using the Portal Base URL.
- After configuring all other required fields, click OK. Then, click SAVE on the Edit SAMLSettings window.